Enterprise JavaScript: Opportunities, Threats, Solutions
June 21st, 2019 | By Jscrambler | 4 min read

Enterprise JavaScript Apps have opportunities, threats, and solutions, as they are for web, mobile, and desktop apps with cross-platform development.
If you're working with JavaScript, it's entirely likely that you're familiar with its history. The 24-year-old programming language has evolved drastically over the past few years, especially with the advent of Node.js and JS frameworks.
If JavaScript was a gimmick that made websites dynamic and more enjoyable, today the panorama is quite different. JavaScript is the powerhouse of the web.
A staggering 97% of modern web apps use JavaScript, and every single Fortune 500 company relies on Node.js and JavaScript to create highly competitive web and mobile applications.
With the fast adoption of Progressive Web Apps as a viable alternative to native apps, it appears that this growth will indeed accelerate. JavaScript is not only for the web but also for desktop and mobile devices with cross-platform development.
With all its numerous advantages and business value, we must still consider the other side of the coin: the considerable security threats linked to using JavaScript.
JavaScript: Threats
JavaScript needs to be rendered by a browser in order to work. This means that it can't be encrypted in a feasible way. Then, JavaScript code is completely exposed and anyone can access, read, and modify it.
At first glance, we could argue that this won't be a problem as long as companies don't store important business logic on the client-side. But server calls take time, and in services where performance is crucial, such as streaming, e-commerce, or gaming, this is not an option. Hence, proprietary algorithms are placed on the client-side for the sake of performance.
When we combine these two ingredients — proprietary algorithms and an exposed environment — we get a recipe for disaster. For long, malicious actors have exploited exposed JavaScript, stealing this code and re-distributing copycat apps. But that's just the tip of the iceberg.
Exposed JavaScript opens the door to automated abuse. For instance, a cloud provider may offer 1 month free for new accounts and this can be abused by malicious actors through automated account creation. This is especially relevant in use cases where relying on CAPTCHAs is not feasible.
In an attempt to control account takeover and fight off fraud, several companies deploy JavaScript agents that fight off bots or provide device fingerprinting. However, because these agents' code is also exposed, attackers can reverse-engineer it to bypass them altogether.
Then, we have the case of cheating and piracy. Attackers can take advantage of exposed JavaScript to bypass app restrictions, unlock new features without paying, or violate licensing agreements — all of which pose a threat to a company's business model.
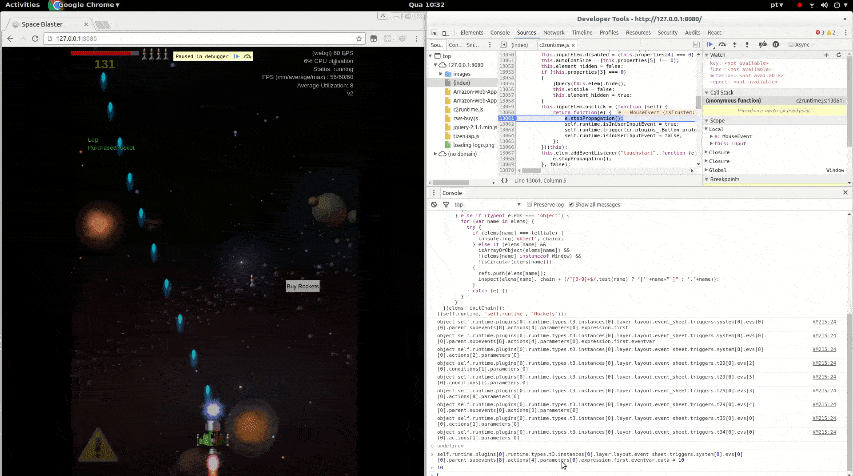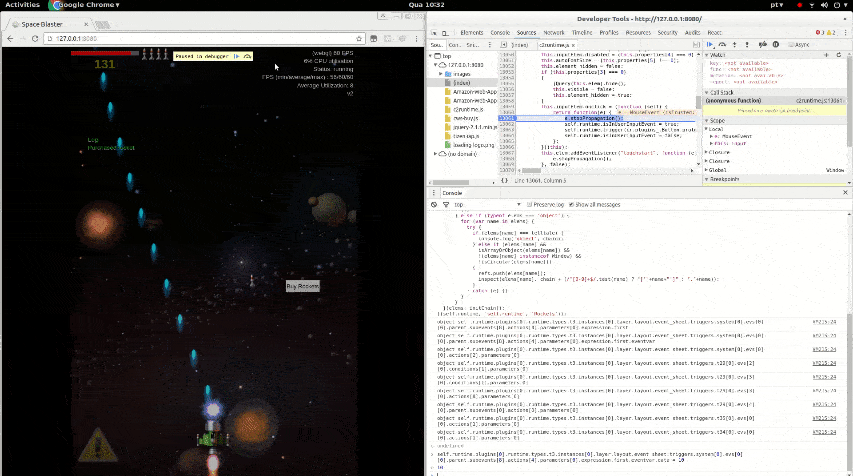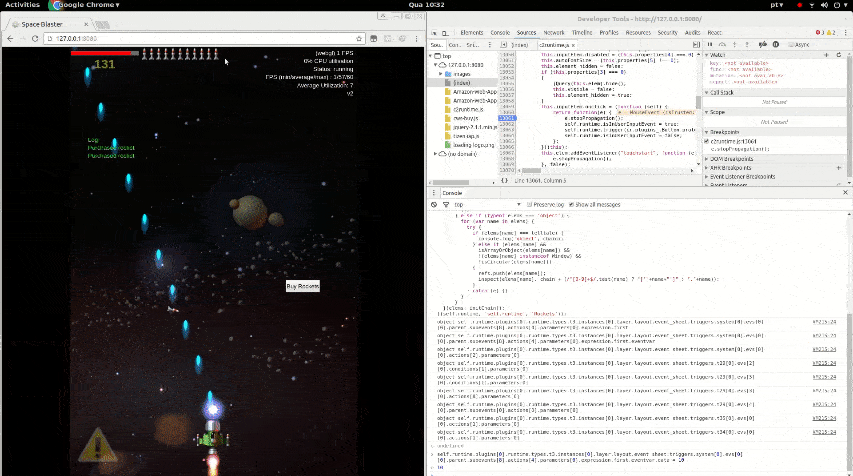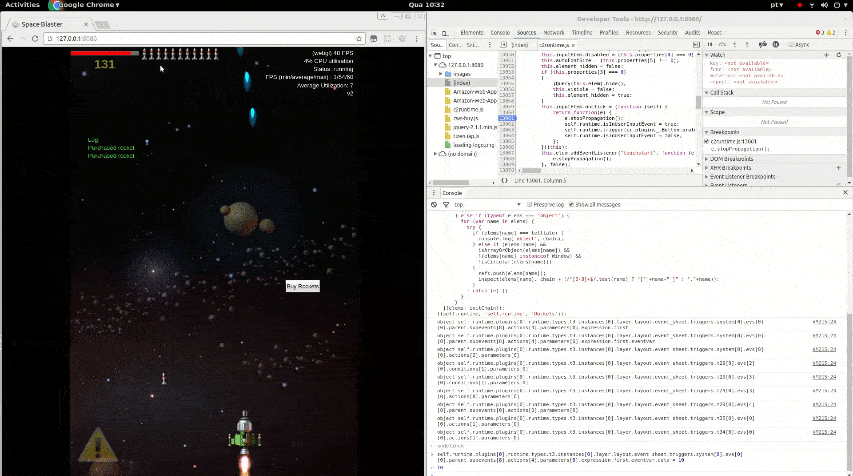
Reverse engineering the source code of a game to bypass a paywall.
The case of licensing agreements and copyrights is especially important for digital content such as video or audio streams. By accessing the underlying JavaScript of HTML5 web players, attackers can capture and redistribute streams, which results in massive business losses for streaming providers.
So, enterprises rely on JavaScript to develop apps that are core to their business but leave their core logic and proprietary algorithms exposed to attacks. Again, they have no way of encrypting this code. What they can do, though, is protect JavaScript with a series of layers that prevent all aforementioned attacks.
JavaScript: Solutions
When we address the threats of code theft and reverse engineering, the only feasible way of protecting JavaScript is by concealing its logic. This is a recommendation by OWASP on their Mobile Top 10 Security Risks, M9-Reverse Engineering:
In order to prevent effective reverse engineering, you must use an obfuscation tool.
JavaScript obfuscation is a core step in protecting JavaScript source code. Obfuscated JavaScript is extremely complex to read, understand, and reverse engineer. But different JavaScript obfuscators provide highly different levels of protection and development teams often struggle to understand which tool to use. Free obfuscators offer basic transformations that can easily be reversed using automated tools.
When deciding which obfuscation tool to use, besides considering the cost of the tool, you should ask yourself:
What would be the cost for my business if an attacker were to re-distribute my code, tamper with it, or bypass our licensing agreements?
Then, we must still consider the more advanced and dangerous threats of application abuse, cheating, and piracy. Free obfuscators offer no real protection against these. Again, enterprise-grade problems require enterprise-grade solutions.
Jscrambler is a market-leading JavaScript protection solution for the enterprise. Not only does it provide the most advanced set of obfuscation techniques, but it also adds three additional protective layers to mitigate debugging and tampering attempts:
Code Locks — Varying application locks that restrict when, where, and by whom your JavaScript application can be executed.
Self-Defending — When your protected code faces a debugging or tampering attempt, Jscrambler’s integrity checks break the application or trigger a countermeasure specified by you.
Self-Healing — Runtime integrity checks that automatically revert tampered code back to original, clean code, without breaking the app or interfering with the user experience.
The combination of these unique technologies effectively mitigates any form of abuse, cheating, piracy, code theft, and reverse engineering attempt that operates through the client-side. This technology has earned the trust of Fortune 500 companies which, along with over 43,000 other companies and individuals, trust Jscrambler to protect their applications.
Looking Ahead
The future looks promising for JS. The enterprise keeps raising the bar by delivering highly advanced user experiences on the web and mobile by leveraging JavaScript's ubiquity, flexibility, and extremely active community.
While we can expect malicious actors to go after these apps for their own gain, companies can (and should) take action to conceal their code logic and actively thwart debugging and tampering attempts. And, unlike some argue, it's not a matter of security through obscurity — it's a matter of adding a new security layer to further protect critical business assets.
If you're interested in knowing how Jscrambler fits your specific use case, book a demo to see our solutions in action, conducted by our application security experts.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
10 Classic Games Recreated in JavaScript
Childhood memories associated with video games can be revived with the help of JavaScript. Fall into nostalgia and find out more!
May 17, 2022 | By Jscrambler | 4 min read
12 Useful JavaScript Newsletters
With so much happening in the JS ecosystem, it's not easy to stay on top of things. Here are 12 newsletters to bring the best news straight to your inbox.
February 10, 2022 | By Jscrambler | 5 min read

