Browser-in-the-Browser: A New Wave of Picture-in-Picture Phishing Attacks?
April 22nd, 2022 | By Jscrambler | 5 min read

Browser-in-the-browser (BitB) attacks have different approaches, usually targeting credentials. Today, we will explore more about this deception technique.
As a new phishing technique, it belongs to a universe of social engineering attacks responsible for more than 80% of the reported security incidents.
What is a browser-in-the-browser attack?
The main goal of a browser-in-browser attack is to lure the user into accessing a cloned website with a fake window, taking advantage of the growing usage of single sign-on systems that allow users to log in to different websites with a single account.
This “fake window” is created inside the website viewport and will replicate very accurately all the components of the popup window.
Some aspects of this method are the URL that can show any URL, the Certificate Lock, and the draggable effect.
In the image below, we can see an example of a cloned website using this technique. The highlighted sections show how visually accurate this window can be.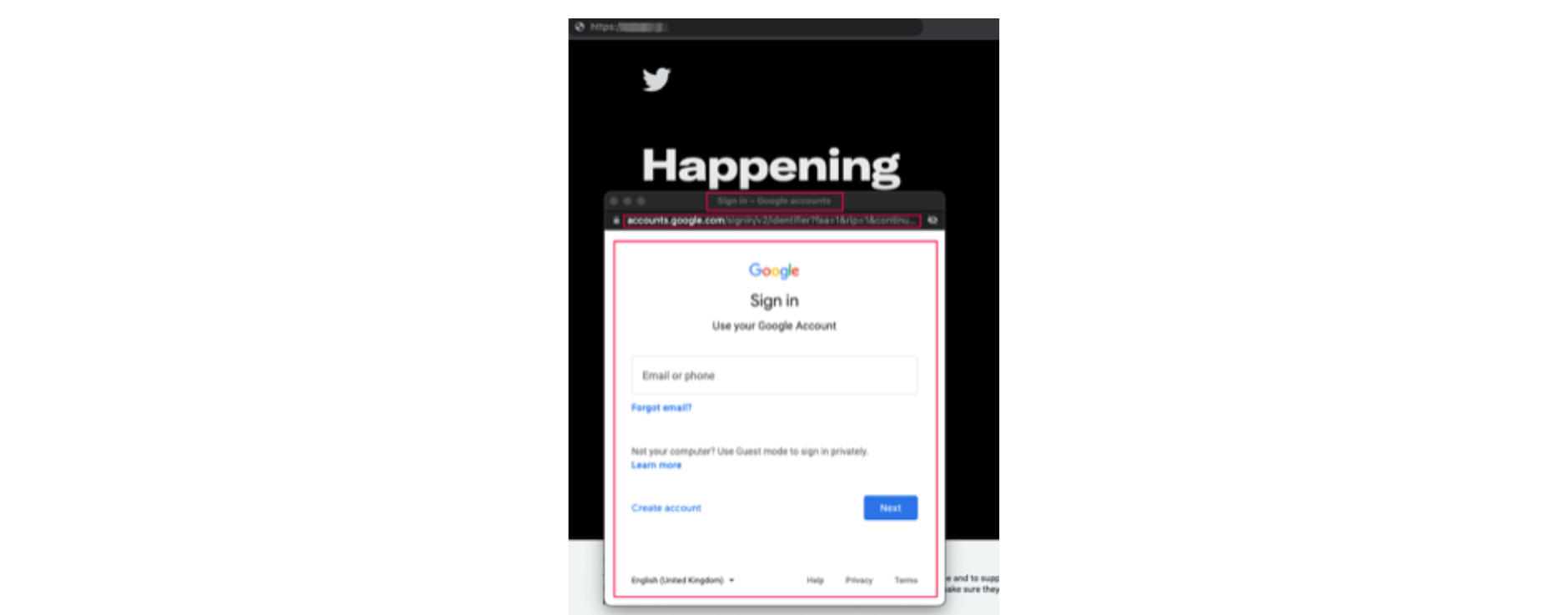
This approach is not new. We can trace it back to some attacks in the past two decades.
In 2019, a fake Steam skins giveaway site was used to steal credentials from Counter-Strike players, but this was not a singular event.
Facebook was also targeted in phishing campaigns using this technique. Going back to 2007, we can find remarks about a “picture-in-picture attack” referred to in a Microsoft publication. They claim that “picture-in-picture attacks showing a fake browser window were as effective as the best other phishing technique, the homograph attack.”.
Other approaches to this deception technique
While the BitB technique is being used in the wild on fake cloned websites, there are several other scenarios where a similar method could be applied, for instance, in the case of a supply chain attack.
Browser Extensions
There is no doubt that browser extensions provide a great way of customizing your web browser or even enhancing the functionality of a website.
Nowadays, the user will most likely have an ad blocker, a password manager, or a cryptocurrency wallet extension installed in the browser. As helpful as they can be, some of them may also pose a security risk.
Suppose a malicious script draws one of these extension windows on a webpage, similar to the BitB attack we described before.
An unaware user may look at this window and mistake it for the legitimate one, inserting his credentials or keys and naively sending them to the attacker.
Browser Notifications
Even though this type of notification does not typically ask the user to type any information inside the notification window, a fake one could make the user click on it.
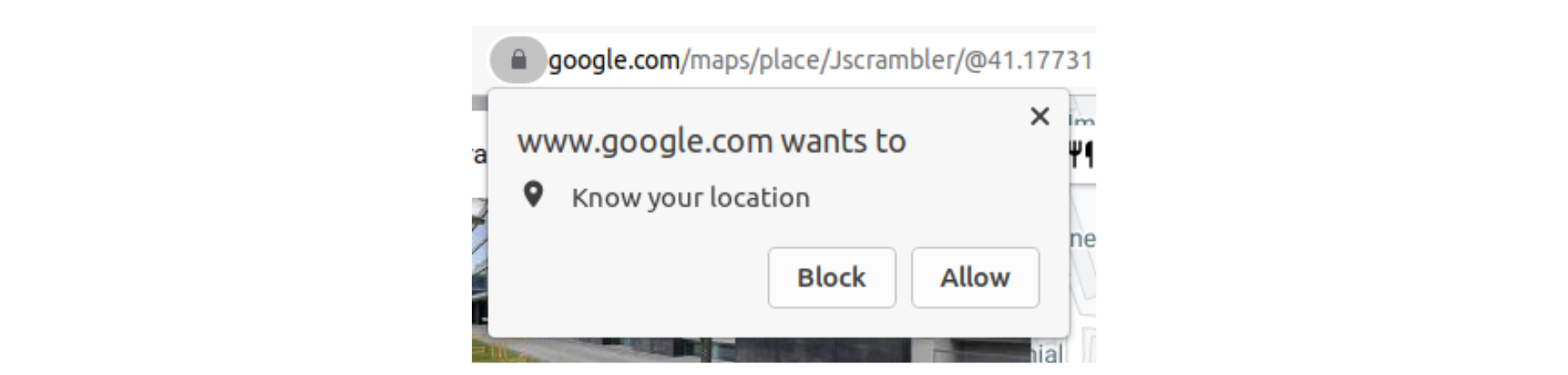
Clicking on something different from what the user perceives, known as clickjacking, is one of the potentially dangerous attacks that can be used to reveal confidential information or trigger unintended behavior by the website or browser.
Sometimes clicking on seemingly innocuous objects may allow an attacker to take control of your computer.
Javascript alerts
Some applications may use JavaScript functions like alert, confirm, or prompt to ask the user for important information. These functions will trigger a box to appear, usually on the upper part of the screen, but this may vary depending on the supplied text message.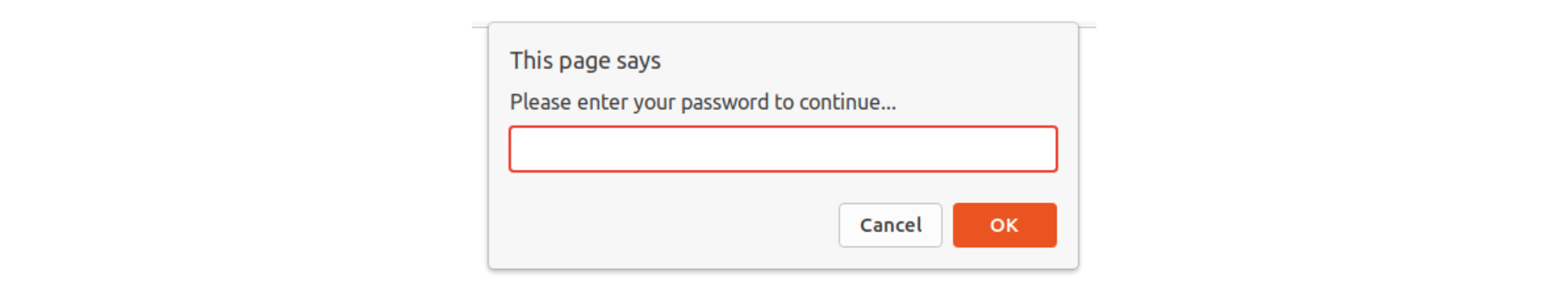
This is another example of a window that can be drawn inside a webpage, inviting users to type private information.
Summing Up
As we can see, there are a lot of deception techniques that can lure the user into performing unwanted operations. But some things can be done to mitigate this.
From a company perspective, organizations are responsible for the user experience they provide and the security of their applications. Thus, they should implement systems or mechanisms into their web pages to mitigate some of these attacks.
In short, the type of attacks we saw consisted of:
Creating and appending elements, e.g., creating an iframe
Poisoning functions, e.g., alter login function
Editing element attributes, e.g., changing a link
And these kinds of malicious behaviors can be detected or even blocked if a client-side security solution is implemented on the web pages.
User-Awareness Guidelines
Even though we are describing attacks that may deceive even the savviest users, there are a few subtle clues that can be used to detect this kind of attack.
Users can click the suspect window title bar and drag it around the screen. A legitimate window can be dragged anywhere without limitations, whereas a fake window will stay within the boundaries of its parent browser window.
Users can hover the mouse cursor over the browser icon in the taskbar. If the popup is a real browser window, there should be (at least) two instances of the browser running, but if not, then the user would only see one instance.
Users can right-click the title bar of the suspect window. The context menu of a legitimate popup should display window-related options like New Tab or Close, but a fake window will show content-related options like Back, View Page Source, or Inspect.
Users can look for active or focused windows. There should only be one active window at a time. A fake window will appear focused while the real window is still focused.
Conclusion
Many companies protect their users with client-side solutions like the Webpage Integrity by Jscrambler. These solutions provide an additional layer of protection that will render most of these attacks unfeasible or impractical.
But most websites do not have this kind of protection, and the responsibility is left to the user. This is why User awareness is crucial for user and information security.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Man in The Browser Attacks: A Comprehensive Guide
With a rapidly growing user base on the Internet, potential attackers have new, innovative, and complex ways to serve their malicious purposes. One such attack is MitB.
February 22, 2017 | By Shaumik Daityari | 5 min read
Why You Don't Know The Client Browsers
With the proliferation of JavaScript on the client, modern solutions put more and more business logic on the client and this has implications for security.
January 12, 2017 | By Camilo Reyes | 4 min read
