The Security Risks Associated With CAPTCHAs
August 26th, 2025 | By Ejiro Thankgod | 15 min read

The cybersecurity field depends heavily on CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), which has proven its importance for many years. CAPTCHAs operate as a digital wall system to stop robotic attack attempts while allowing genuine human users to secure specified web services. The security tool known as CAPTCHA evolved from text-based methods into contemporary reCAPTCHA systems.
The rise of advanced cyber threats has raised doubts about the effectiveness and security measures of CAPTCHA systems. CAPTCHA partially mitigates security risks, but the technology also presents an attractive attack target, introducing multiple security and usability difficulties. This paper examines undisclosed security hazards in CAPTCHA alongside their claimed protection strength assessment.
Understanding CAPTCHA and Its Role in Security
CAPTCHAs were first introduced in the early 2000s as a solution against automated website interaction brought by bots. Each CAPTCHA test consists of difficulty levels that minimize the ability of machines to mimic human perception activities.
CAPTCHAs serve as a protective barriers that allow humans to continue while blocking computerized systems. This protection is crucial for numerous online scenarios:
Preventing automated account creation and spam registration
Protecting login systems from brute force attacks
Safeguarding forms from spam submissions
Preventing automated scraping of content
Securing ticket sales and limited-quantity purchases from bots
Protecting polling and voting systems from manipulation
The foundation of CAPTCHA effectiveness depended historically on what computers could not perform as well as people did. CAPTCHA functions as a security measures that deliver tests that computers find complex, while human users can solve them easily. Various versions have been developed throughout time, which include:
Text-based CAPTCHAs

The original and most recognizable form of CAPTCHA presents users with distorted text that must be correctly identified and entered. These systems use various obfuscation techniques:
Character warping and distortion
Addition of noise, lines, or background patterns
Overlapping characters
Varied fonts and sizes
Character rotation and perspective shifts
Text-based CAPTCHA systems that were considered adequate until recently fail due to the sophistication of OCR (Optical Character Recognition) algorithms. Modern machine learning models exceed 99% success rates on text-based systems, thus making these CAPTCHA versions outdated for high-security purposes.
Image-based CAPTCHAs
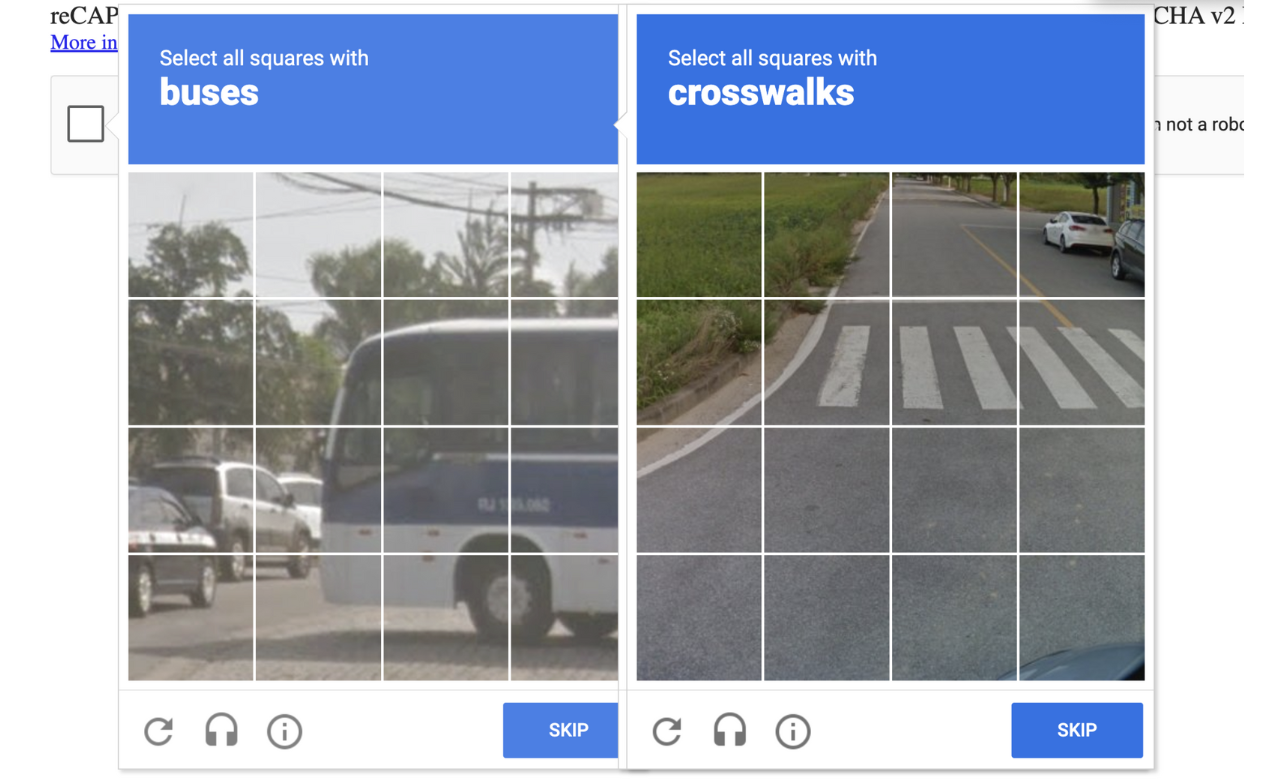
As text-based systems became more vulnerable, image recognition CAPTCHA emerged as a stronger alternative. These typically present users with a grid of images and ask them to identify specific content. Common variants include:
Selecting all photos containing a particular object (e.g., "Select all images with traffic lights")
Identifying a specific category of images (e.g., "Select all animals")
Arranging images in a logical sequence
Identifying the odd image out from a set
The reCAPTCHA v2 system from Google introduced human-image recognition assessment to exploit the performance discrepancies between people and computers. Sophisticated neural networks combined with computer vision systems have caused the recognition gap to decrease significantly. Technology today has developed AI systems that match human performance when recognizing images in multiple use cases.
Audio CAPTCHAs
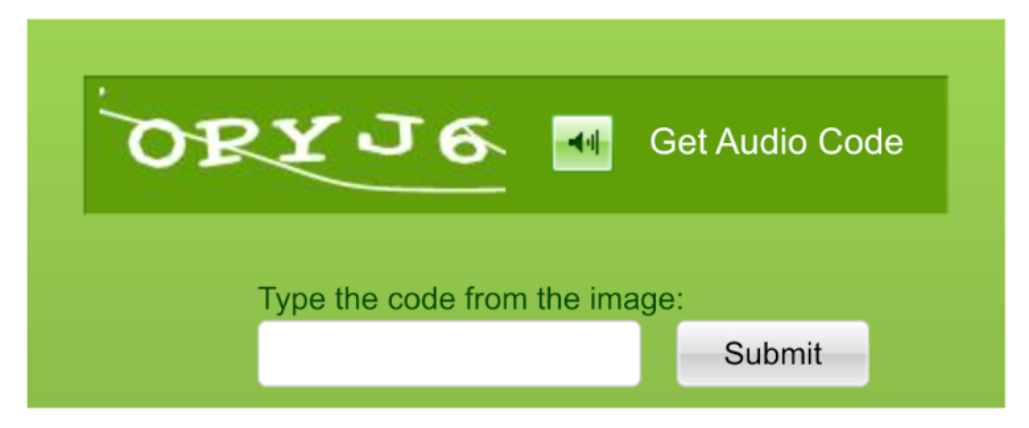
Developed primarily as an accessibility alternative for visually impaired users, audio CAPTCHA presents spoken characters or words, often with background noise or distortion. Users must listen to the audio and type the spoken content.
The accessibility feature of audio CAPTCHA makes it susceptible to attacks from speech recognition systems, which have proven their effectiveness at defeating the system. Among the tasks these modern speech-to-text tools perform is the perception of distorted audio at a level beyond human ability, especially when background noises interfere.
Interactive and Puzzle-Based CAPTCHA
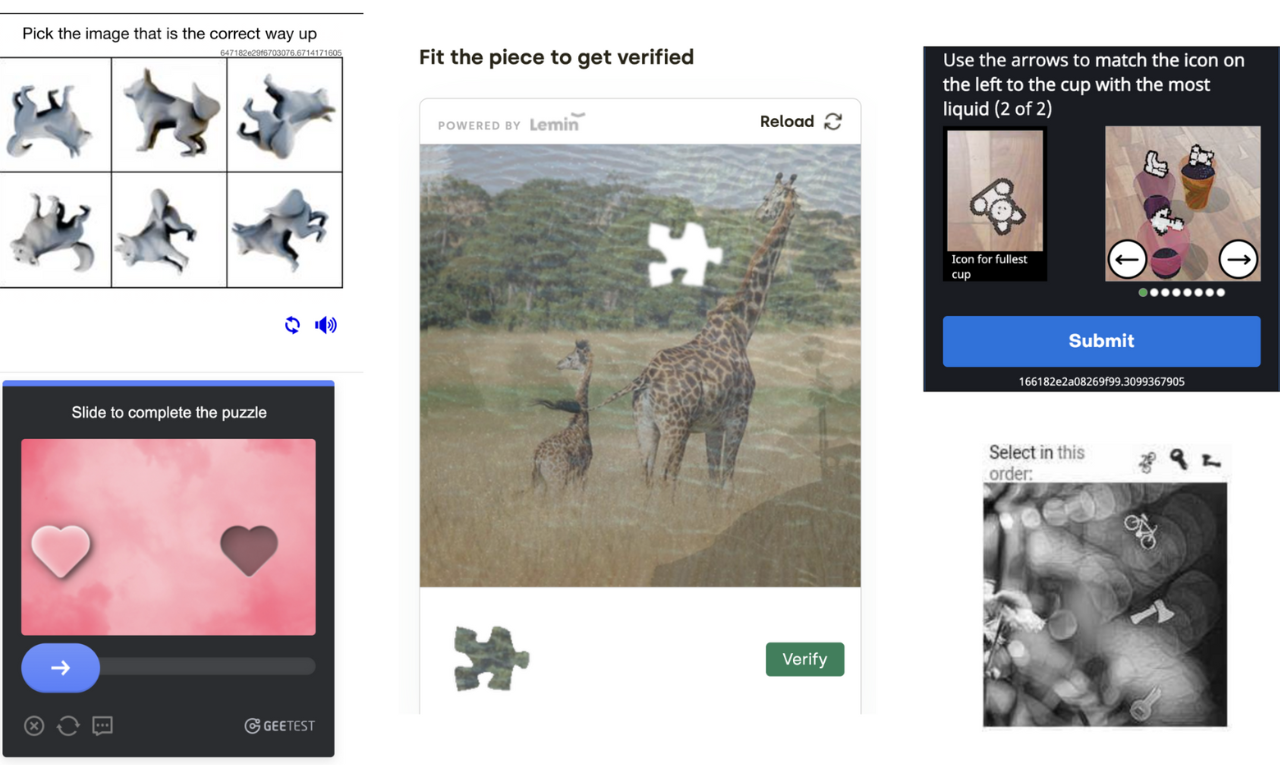
These systems combine direct user interaction with problem-solving elements, creating a more engaging verification experience. They require users to perform specific manipulations or solve visual puzzles:
Sliding a puzzle piece into the correct position
Rotating images to achieve proper orientation
Dragging and dropping elements in a logical sequence
Jigsaw puzzles where users must assemble fragmented images
Matching games require users to pair related items
Pattern completion tasks
Companies like FunCaptcha (now Arkose Labs) pioneered this approach, creating game-like verification experiences that attempt to balance security and user experience. These systems often analyze not just whether the puzzle was completed correctly, but also how it was finished, adding behavioral analysis as an additional security layer.
Behavioral/reCAPTCHA (v2, v3, Invisible)
The latest evolution in CAPTCHA technology has moved toward passive, behavioral analysis rather than explicit challenges.
Google's reCAPTCHA v3 assigns risk scores based on user behavior without requiring explicit verification.
Behavioral systems analyze mouse movements, typing patterns, and navigation behavior.
"Invisible" CAPTCHAs run in the background, only triggering visible challenges when suspicious activity is detected.
The latest systems deploy machine learning algorithms to distinguish between human behavior and bots, providing users with enhanced security without compromising the user experience. Security concerns about privacy emerge due to how these systems gather and interpret large amounts of behavioral user data.
4 Security Risks Associated with CAPTCHA
While CAPTCHAs are designed to protect websites and users from automated threats, they are far from infallible. Open-source technology and resourceful cybercriminals continue to advance together, which creates security risks from CAPTCHA that both diminish their protective functions and produce new system vulnerabilities. The security weaknesses in online systems stem from both CAPTCHA limitations and malicious exploitation techniques that expose vulnerabilities, thereby compromising security, privacy, and trust in online systems.
1. CAPTCHA Solving Services and AI Advances
The development of AI alongside machine learning has improved automated tools so they can defeat CAPTCHA. Security providers who operate under the names of CAPTCHA solvers use either artificial intelligence techniques or low-cost human resources to bypass CAPTCHA barriers easily. Some key risks include:
AI-Powered Bots: AI models can now process distorted text and recognize images with a high degree of accuracy, rendering traditional CAPTCHA ineffective.
Cheap Human CAPTCHA Solving Services: Cybercriminals exploit services that utilize human workers to solve CAPTCHAs at minimal costs, thereby defeating their intended purpose.
Increased False Positives: More sophisticated CAPTCHAs often become overly complex, mistakenly blocking legitimate users while still being vulnerable to bots.
2. CAPTCHA Exploitation by Cybercriminals
Rather than deterring attackers, CAPTCHAs can sometimes be leveraged for malicious purposes, including:
Phishing Scams: Cybercriminals create fake CAPTCHA pages on phishing websites to lull users into a false sense of security before stealing login credentials.
Man-in-the-Middle (MITM) Attacks: Malicious actors intercept CAPTCHA responses, using them to gain unauthorized access to systems.
Malware Deployment: Some malicious sites present CAPTCHAs to make users believe they are interacting with a legitimate service before infecting their devices with malware.
3. Privacy and Data Collection Concerns
Many CAPTCHA systems, particularly Google’s reCAPTCHA, rely on extensive tracking of user behavior, leading to serious privacy concerns. These include:
Tracking Browsing Behavior: reCAPTCHA monitors how users interact with web pages, collecting data about their browsing habits.
Google Account Dependencies: Some CAPTCHAs require users to be logged into Google, linking their activities to their Google account.
User Profiling: The data collected can contribute to fingerprinting techniques, raising ethical concerns regarding user privacy.
4. User Experience and Accessibility Issues
CAPTCHAs often degrade user experience and accessibility, leading to frustration and potential exclusion of certain users:
Frustrating Challenges: Many CAPTCHA are difficult to solve, leading to form abandonment and reduced conversions.
Accessibility Barriers: Visually impaired and dyslexic users struggle with text- and image-based CAPTCHAs, while audio CAPTCHAs often suffer from poor quality.
Increased Cognitive Load: Users with cognitive disabilities may find CAPTCHAs overwhelming, making online interactions more difficult.
Emerging Threats and Mitigation Strategies
The security effectiveness of CAPTCHAs has declined due to advanced security challenges that have breached its traditional standards. The advancement of technology, together with attacker development, exposes design weaknesses in CAPTCHA systems by creating new threats beyond their original capabilities. At the forefront are AI-driven innovations, but other risks lurk in the shadows, demanding creative and robust responses. New mitigation strategies develop to confront these threats directly by enhancing or developing alternative CAPTCHA-based security systems.
AI-Powered CAPTCHA Breaking
Artificial intelligence has turned the process of breaking CAPTCHAs into a sophisticated practice. Deep learning tools and generative AI enable bots to break text-based CAPTCHAs through OCR, analyze image grids using neural networks akin to human vision, and replicate mouse click actions for behavioral CAPTCHAs. Attackers obtain access to CAPTCHA-solving tools through commercial plug-and-play and cloud services which make defeating CAPTCHA easier for a wide range of attackers leading to increased operational scale.
Here, we can see below how an AI-powered CAPTCHA solver works, such as a bot quickly solving an image-based CAPTCHA.

Here is another example below:
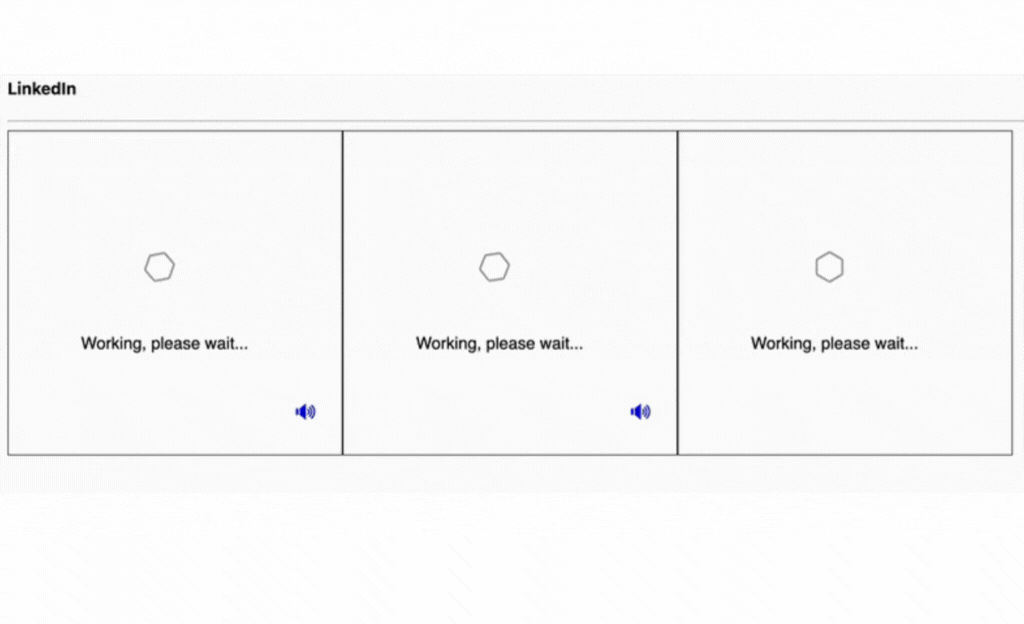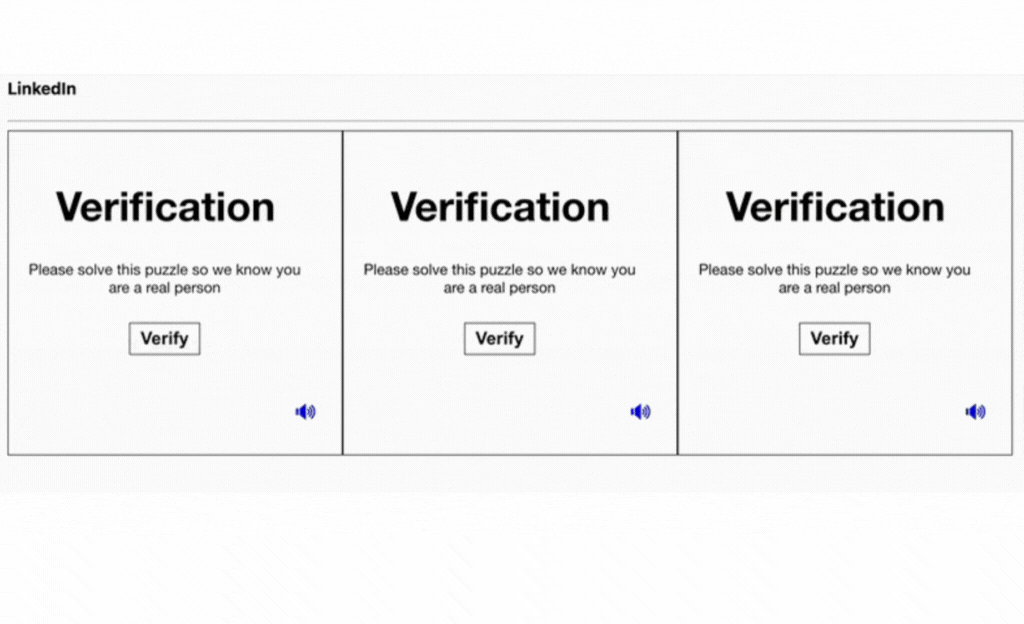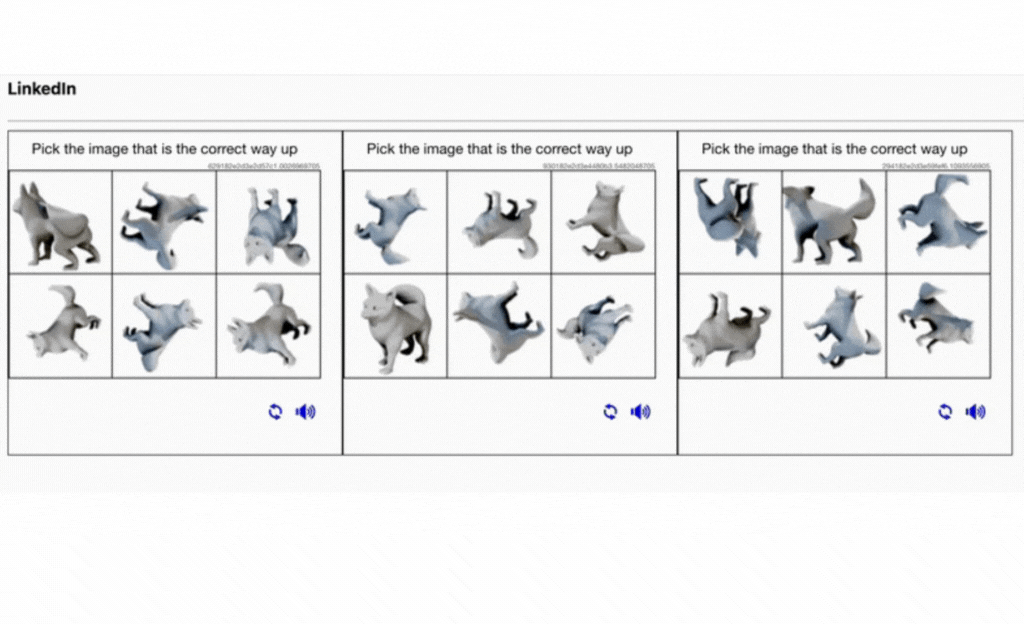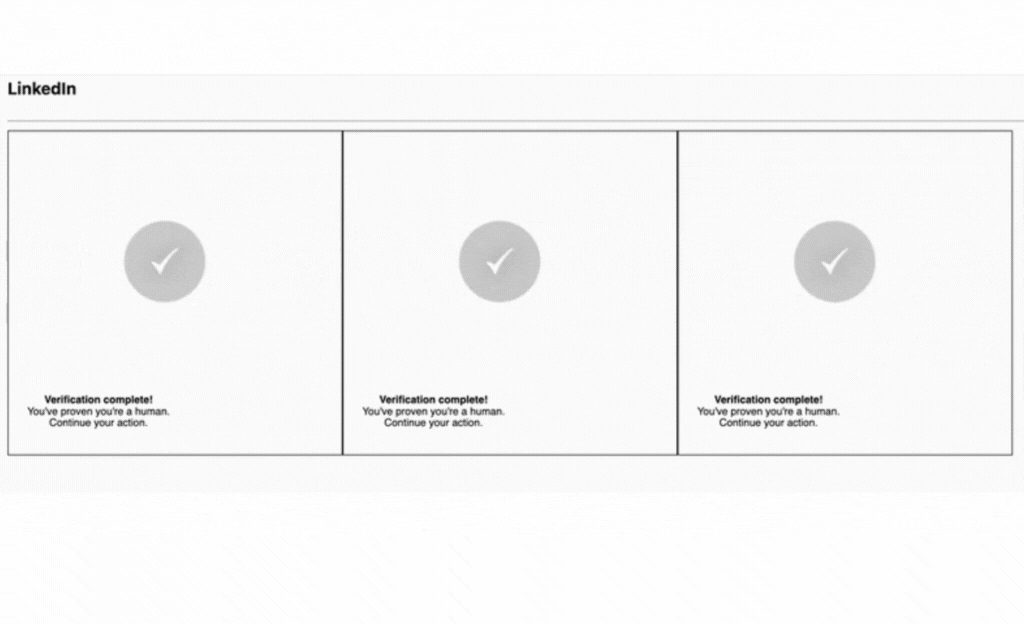
AI solvers achieve up to 90% success rates on text and image CAPTCHAs. Google’s reCAPTCHA v2 and v3 have been bypassed using AI-powered bots. The effectiveness of CAPTCHAs declines rapidly, forcing businesses to look for alternative security measures.
Beyond AI, additional dangers loom. Crowdsourced CAPTCHA bypassing leverages human workers via CAPTCHA farms, blending automation with low-cost labor to tackle complex challenges. Zero-interaction exploits target backend flaws—like unvalidated server responses or vulnerable APIs—allowing attackers to skip CAPTCHAs entirely. Meanwhile, user behavior shifts driven by frustrating CAPTCHAs push legitimate users toward insecure workarounds or phishing traps, indirectly amplifying risks. Together, these threats form a multi-front assault on CAPTCHA reliability.
The importance of a layered security approach
The battle requires combined security measures since any single method proves insufficient on its own. Security against attackers becomes more challenging when CAPTCHAs are combined with multi-factor authentication (MFA), which requires text codes or biometric authentication. Adding intrusion detection, rate limiting, or IP reputation checks further fortifies defenses. This approach reduces pressure on CAPTCHAs as the sole gatekeeper, distributing security across complementary layers to catch what slips through. It’s a holistic mindset: diversity in protection breeds strength.
Alternative Solutions to CAPTCHAs
Organizations need to find substitute security measures to improve defense capabilities while maintaining user comfort through the ongoing struggles of CAPTCHAs against artificial intelligence and automated bots. Companies operating under these risks should adopt alternative measures to CAPTCHAs, which include:
Biometric Verification: Biometric solutions tap into what’s uniquely human: physical or behavioral traits. Options like facial recognition, voice authentication, or even typing rhythm analysis (keystroke dynamics) verify identity without requiring puzzles.
Device Fingerprinting: Device fingerprinting shifts the focus from user challenges to machine identity. By analyzing a device’s unique traits—browser version, screen resolution, installed fonts, timezone, or even subtle hardware quirks—this method builds a “fingerprint” to verify legitimacy.
Honeypots: Honeypots are a stealthy, user-invisible approach to bot detection. These traps embed hidden fields or links in a webpage—elements that humans naturally ignore but bots, programmed to interact with all available inputs, can’t resist touching.
Multi-Factor Authentication (MFA): Combining passwords with additional authentication steps, such as SMS codes or biometric verification.
Risk-Based Authentication: Risk-based authentication (RBA) ditches one-size-fits-all challenges for a dynamic, context-aware approach. By assessing factors like IP location, login frequency, or device reputation, RBA calculates a risk score. Low-risk users (e.g., someone logging in from a familiar device) breeze through, while high-risk ones (e.g., a new IP from a known botnet) face additional hurdles—perhaps a secondary code or question.
Cryptographic Attestation: For a cutting-edge twist, cryptographic attestation uses hardware-based security—like Trusted Platform Modules (TPMs) or secure enclaves—to prove a device’s authenticity. A website might request a cryptographic token from the user’s device, verifying it’s not a virtualized bot.
Conclusion
Advanced security threats have made CAPTCHA less effective, even though they initially served a critical role in online defense systems. Reliability in CAPTCHA decreases because of the combined impact of CAPTCHA-solving services alongside AI advancements, privacy concerns, and user experience problems. Businesses should look into different authentication and security techniques that combine high protection with ease of use.
Modern technology has created uncertainty about whether CAPTCHAs operate as a protective measure or represents a security risk. Online security demands continuous evolution because threats in the cybersecurity domain keep becoming more sophisticated.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Implementing Google reCAPTCHA V3
In this tutorial, you'll learn how to integrate Google reCaptcha v3 into your Next.js application.
September 17, 2024 | By Jay Raj | 10 min read
Best Practices to Ensure API Security: Why and How?
API security aims to protect APIs from attacks and data breaches. Let's explore the need for API security best practices amid pervasive and emerging cyber threats.
April 22, 2025 | By Tom Vicary | 11 min read
