How to Prevent Data Leakage on Your Website
June 4th, 2024 | By Antonello Semeraro | 7 min read

Understanding data leakage and its consequences is fundamental for anyone who manages or operates a website. However, to effectively combat this issue and prevent data leakage, it's essential to go through the mechanics behind this cybersecurity practice that involves implementing secure data practices to reduce accidental exposure.
Why Do Websites Leak Data?
To address this question, we must first comprehend the workings of the average modern website. According to the latest statistics, approximately 70% of all scripts running on the average website are sourced from third parties, which means that companies have direct control over only about 30% of their website’s code, which is developed and maintained in-house.
Diving deeper into the composition of this first-party code, it's often found to be built using JavaScript frameworks and libraries such as React and Angular. These tools are fundamental to the development and functionality of modern websites, but they also play a role in the broader context of data security and leakage.
![]()
The integration of hundreds of pieces of third-party code into websites introduces a complex supply chain, creating a significant security blind spot for companies. This complexity presents an opportunity for attackers to exploit vulnerabilities and leak data from the website.
But how can attackers exploit this vulnerability?
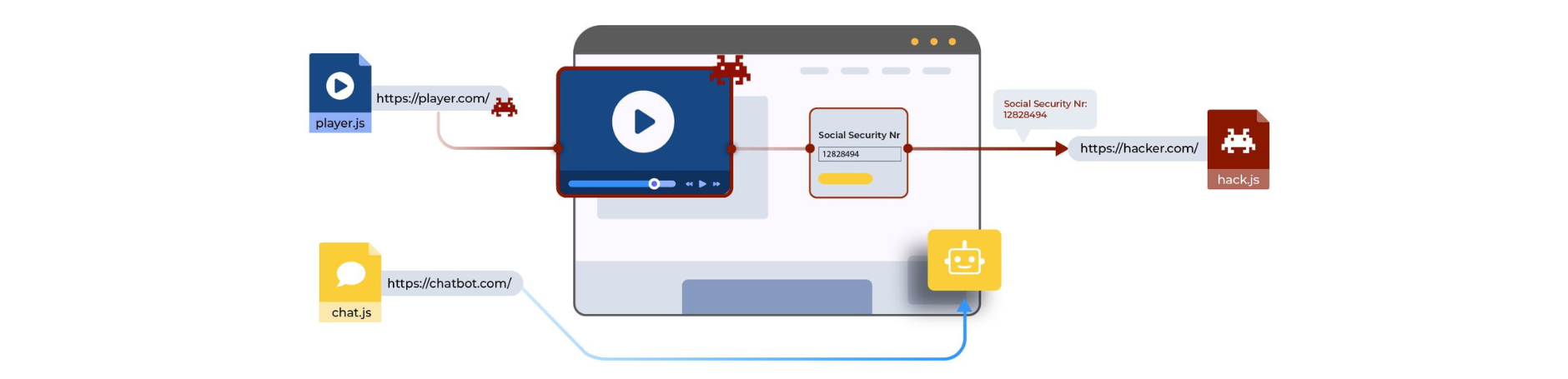
A critical aspect of third-party scripts is their level of access; they possess the same capabilities as the site's first-party code, which means that third-party scripts can access any type of data on the website, modify existing code, and even alter how users interact with the site.
This situation underscores the broader issue of web supply chain security, highlighting the need for stringent measures to safeguard against these vulnerabilities.
The Web Supply Chain and Data Leakage
The integration of external code, from code libraries to third-party services like chatbots, significantly increases the complexity of managing a website's security.
As these pieces of external code accumulate, website owners find themselves with limited or no visibility over the code running on their websites. This lack of visibility becomes a remarkable issue when considering that websites often handle sensitive information, such as credit card details, social security numbers, and private health information.
When users submit this data, it traverses the chaotic client-side environment, potentially exposing it to threats if the website's operators are unaware of the code's behavior on their platform.
This security blind spot has been exploited by attackers to launch web supply chain attacks. These attacks have grown in popularity for a couple of reasons.
Firstly, by altering a third-party script, an attacker can inject arbitrary code into a website, allowing them to perform a wide range of malicious activities affecting all users of the site. This not only compromises the security of the targeted website but also affects other websites using the same third-party script.
Furthermore, web supply chain attacks offer an attractive avenue for attackers because they do not need to target the main website directly. Instead, they can target the weakest link in the security chain: the third-party vendors. These vendors often have fewer resources dedicated to security, making them easier targets.
Protecting the Web Supply Chain and Preventing Data Leakage
To effectively prevent data leakage within the web supply chain, the initial step involves gaining comprehensive visibility into client-side activities, which entails monitoring each script running on your website in real-time to understand its specific behaviors.
A core topic of this process is identifying whether a script is transmitting data, the types of data being sent, and the destinations of this data. Without this insight, distinguishing between legitimate network connections and potential data leakage attempts becomes challenging.
However, achieving visibility is only one part of the solution. A strategic approach to preventing data leakage also necessitates control over the behaviors of your website's scripts, with the ability to impose restrictions by default.
Traditional security measures, such as Content Security Policies, Web Application Firewalls, and browser defenses, often fall short of fully addressing data leakage concerns. Thus, a more comprehensive security strategy that ensures visibility and control is essential.
Gaining visibility starts with conducting an inventory of all scripts running on your website, along with mapping out the network connections they establish, which introduces a detailed overview of your client-side architecture, your exposure to web supply chain risks, and the pathways through which user data is handled.
On the other hand, achieving control requires the adoption of a solution that enables the restriction of every possible action by third-party scripts without compromising user experience. Jscrambler Webpage Integrity offers a solution with its granular rules engine, which affords the precise level of control needed.
Finally, protecting your source code from data leakage attacks is possible through Jscrambler's Data Exfiltration Prevention countermeasure, granting that any attempt to debug or tamper with your source code results in the immediate blockage of all network connections, safeguarding your users' data.
This method embodies a proactive and in-depth defense strategy against the evolving threats to web supply chain security.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
How To Vet and Manage The Behavior of Third-Party Scripts in Your Website
In this post, we'll explore the current state of web development, the associated risks, and how to vet and manage third-party scripts in your website.
April 22, 2021 | By Jscrambler | 5 min read
Top 5 Biggest Data Breaches and Data Leaks
How do data breaches and data leaks happen? How extensive can their impacts be? Let's explore that and the biggest data breaches and leaks with our list.
March 10, 2021 | By Jscrambler | 9 min read
Data Leakage Prevention Policies: Seal your Security Perimeter
We're exploring the benefits of using a comprehensive prevention tool to proactively manage the deleterious impact of data leakages.
June 2, 2025 | By Tom Vicary | 10 min read
