Jscrambler WPI 101 - Form Fencing
March 25th, 2025 | By Jscrambler | 6 min read

Welcome to our new blog series! Jscrambler WPI 101 is a series of articles about Jscrambler’s product Webpage Integrity (WPI), its main use cases, innovative features, and tips on how to maximize the benefits of using the product.
The focus of this article is the WPI use case for Form Fencing. Forms are integral to many online businesses that sell goods and services online. Forms gather important customer data and allow you to easily collect payment. Before we cover how WPI’s Form Fencing works, let’s see what kind of forms Webpage Integrity protects and the ways in which they are deployed on websites. In the section below, we’ll primarily review the payment forms as they collect the most sensitive data that criminals target - cardholder data.
Form Fencing: The Dangers of Form Data Leakage
Safeguarding user data is critical. Websites rely on third-party analytics libraries to track user behavior, but these integrations can sometimes become a security liability. Let’s imagine that there is a website that uses a third-party analytics library to store user session data. While this functionality is essential for business insights, it also opens the door for potential exploitation.
Imagine a scenario where the third-party library is compromised by malware. Let’s suppose the attackers manipulate a function to access all form inputs and exfiltrate sensitive information. Initially, the function only stores basic user details like email, user ID, first name, and last name.
However, with the malware in place, additional sensitive data—such as addresses and credit card details—could be stealthily collected and sent to an unauthorized external server, all without detection. This kind of data breach can be catastrophic, leading to identity theft, financial loss, and reputational damage.
Preventing Unauthorized Data Collection with Fencing Rules
To counteract such threats, businesses can leverage WPI’s Form Fencing, a proactive security measure that ensures that only authorized first-party scripts and third-party vendors collect and transmit data. With Form Fencing, organizations can create specific rules to monitor and prevent third-party scripts from accessing form fields.
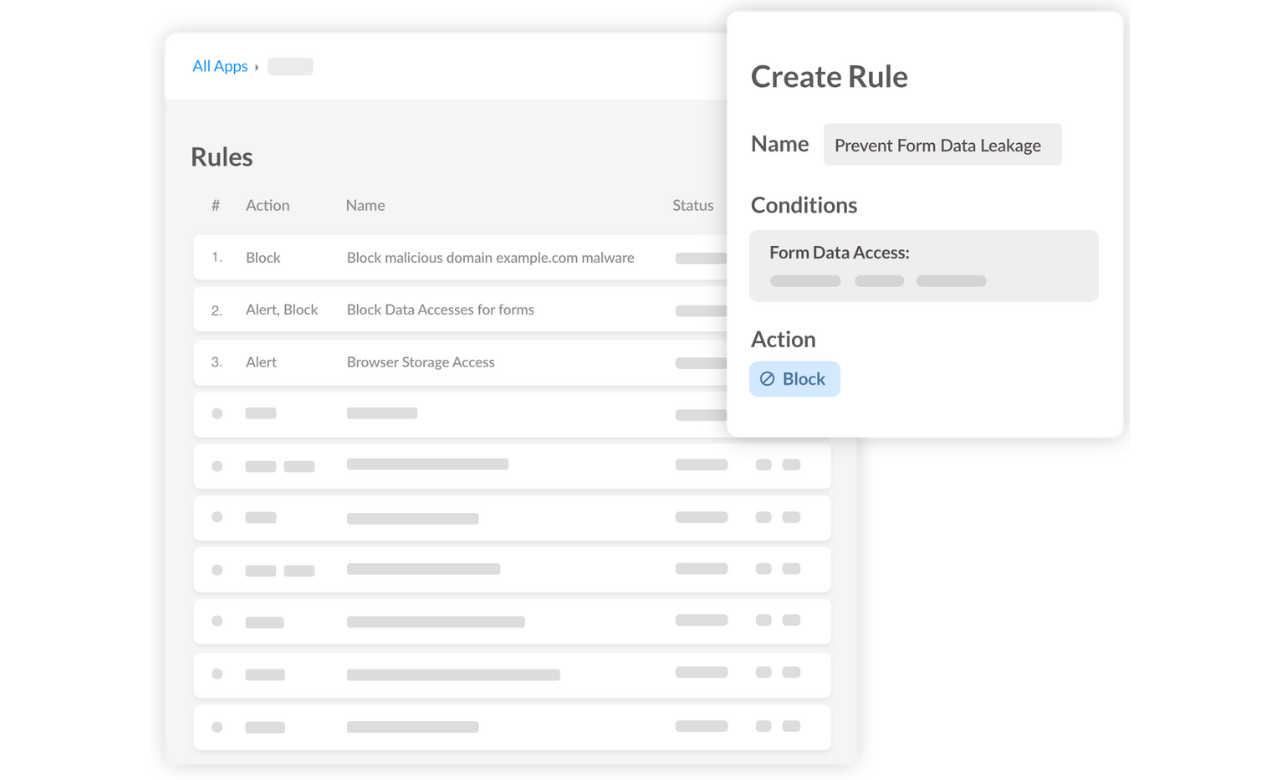
Setting up a Fencing rule is straightforward:
Navigate to the Rules page and create a new rule.
Define a clear name and description for easy identification.
Specify which website pages should be monitored.
Identify the values to configure the rule with the form ID/name or the input ID/name (for example, bookingCode for input booking code and lastName for the input last name).
Configure the targets.
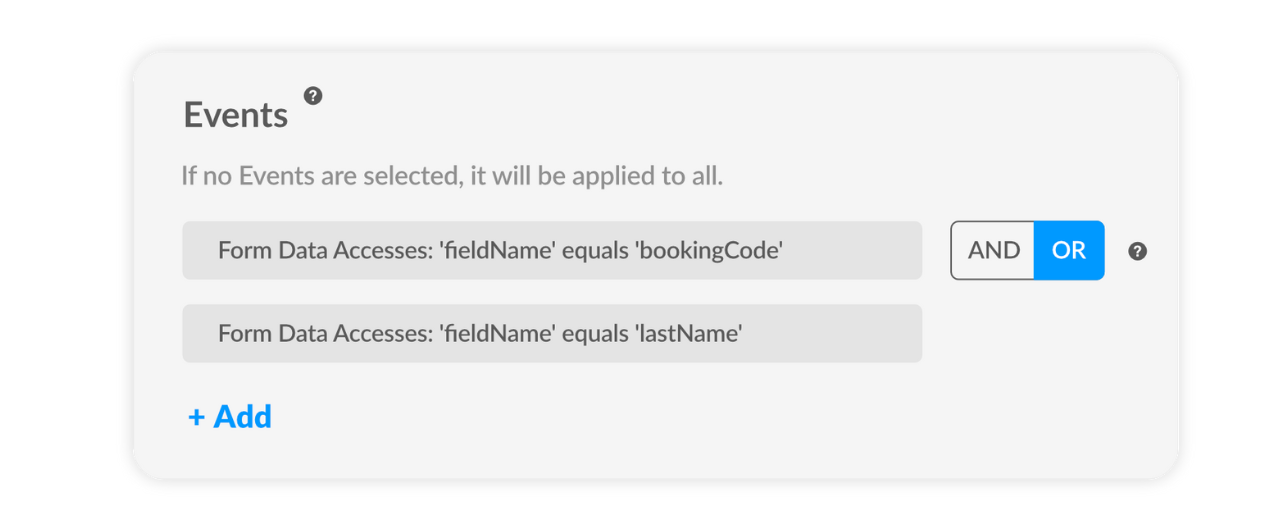
Configure the action to prevent form data from being accessed by unauthorized scripts.
Deploy the rule and activate the WPI protection agent.
Once in place, this rule ensures that any attempt to extract unauthorized information is immediately blocked and flagged in the dashboard.
Payment Form Deployment Types WPI Addresses
There are different ways in which you can deploy a form to be displayed on a website and collect payment data. The most vulnerable forms are usually forms that collect card payment data; they are the most common target of digital skimming attacks. Below are the most common types of payment forms.
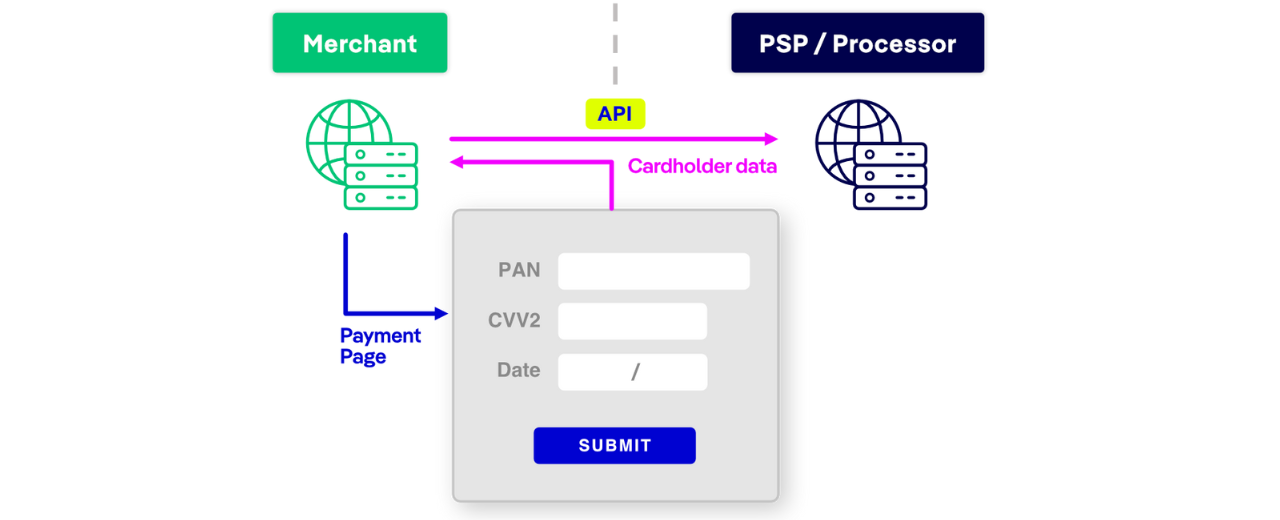
Direct API Integration Forms
Deployment: The merchant collects payment details and sends them securely via an API to the payment processor. In this case, the WPI agent should be injected by the merchant who is responsible for rendering the payment form.
JavaScript-Based Payment Forms
Deployment: A secure JavaScript library (e.g., Stripe.js) collects payment data directly and sends it to the processor. In this case, the WPI agent should be injected by the merchant who is responsible for rendering the payment form.
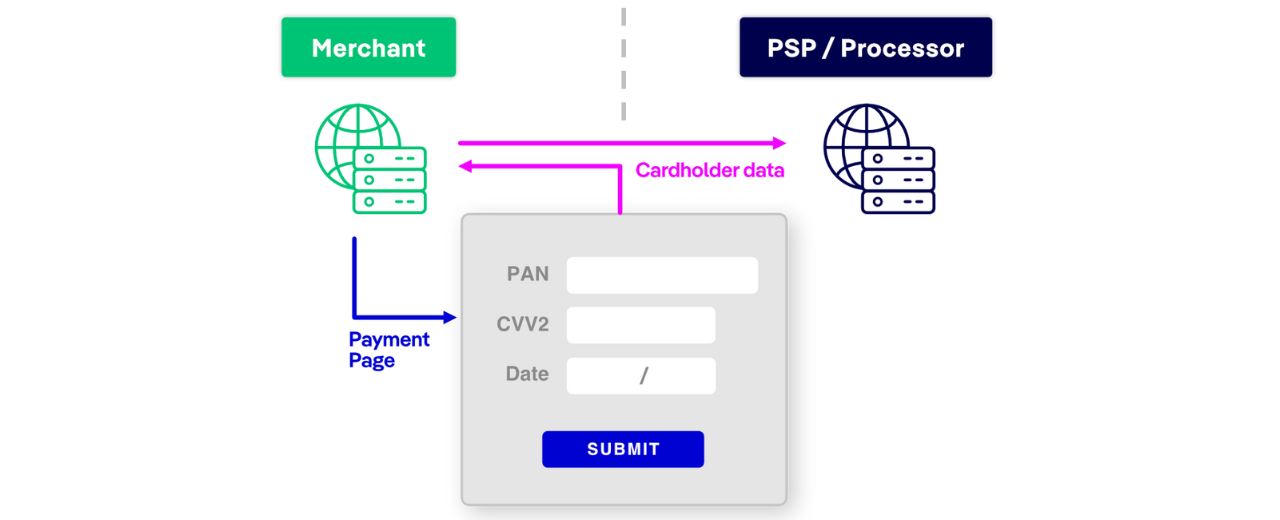
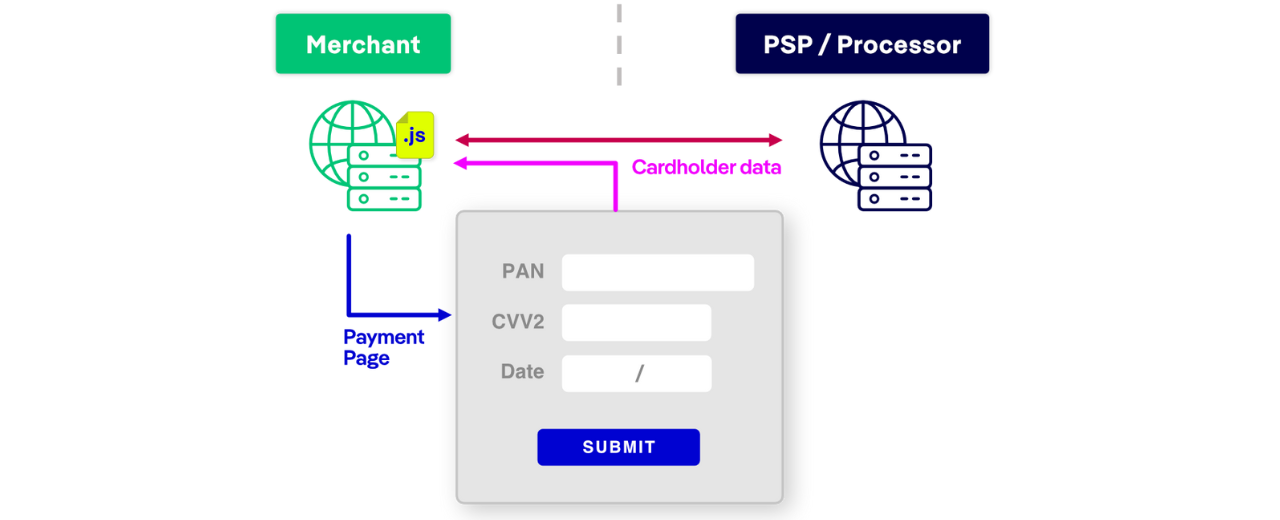
Example: Stripe.js, Braintree Hosted Fields
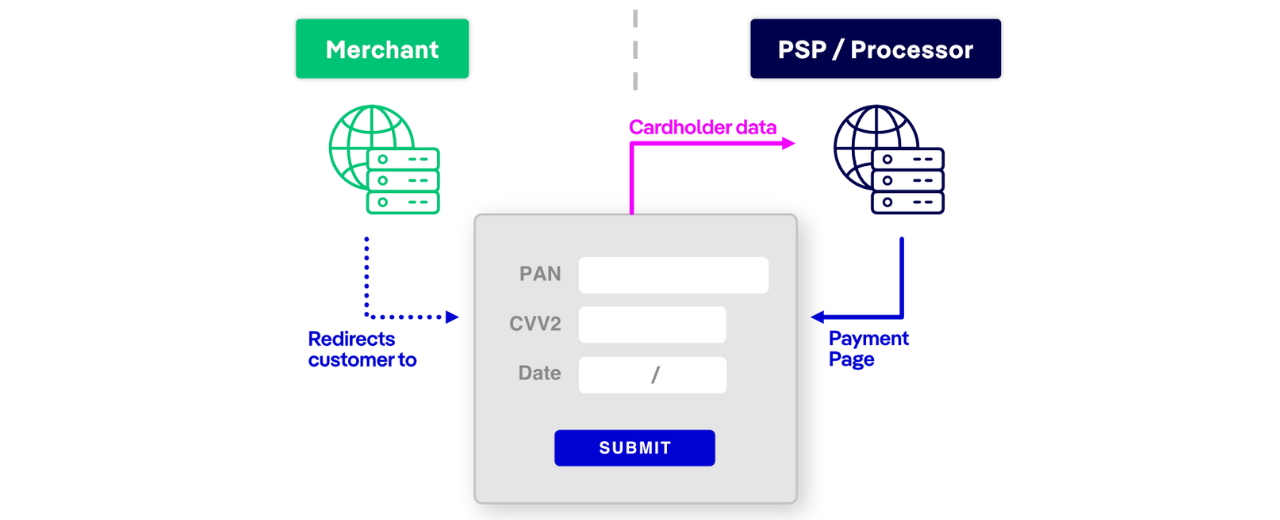
Hosted Payment Forms
Deployment: A third-party payment processor hosts the form, so WPI should be deployed and provided by the Payment Service Provider (PSP).
Form Fencing for PCI DSS v4 compliance
PCI DSS requirements 6.4.3 and 11.6.1 will become effective on March 31st, 2025. Both requirements were developed to ensure that online merchants' payment pages are sufficiently protected to detect and prevent skimming attacks.
If you are a Merchant who hosts a payment form yourself, then you can use a Form Fencing feature as a Compensating Control or follow a Customized Approach to become PCI DSS v4 compliant. Therefore, you don’t need to worry about authorizing scripts.
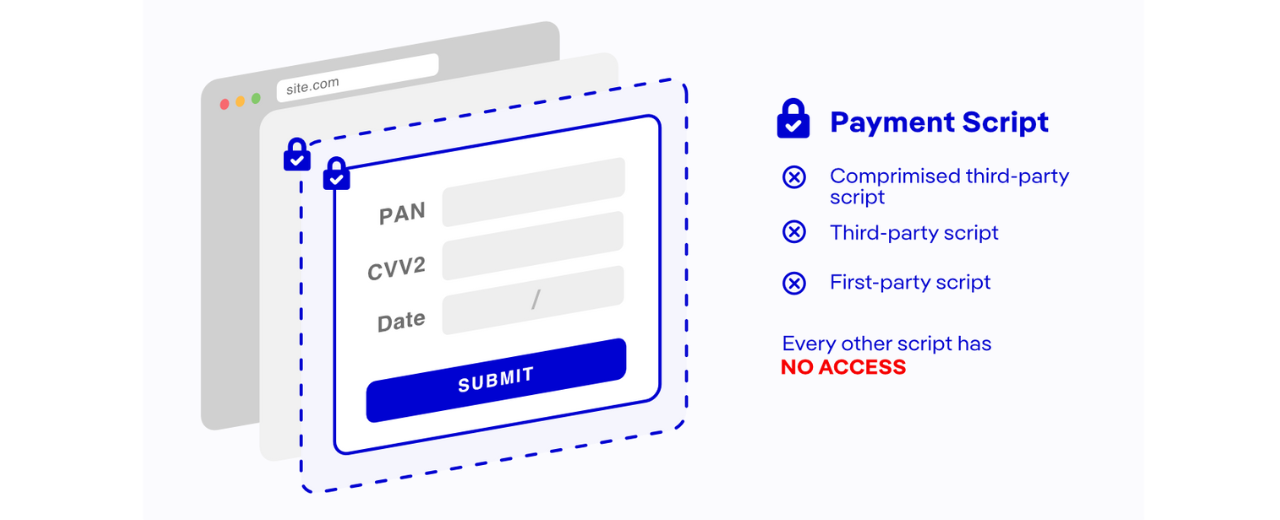
Additionally, Form Fencing works as an extra layer of defense that can shield your forms from skimmers even before you authorize scripts.
As cyber threats continue to evolve, proactive security solutions like Form Fencing are essential in protecting sensitive information. By implementing Form Fencing, businesses can safeguard user data, maintain compliance with data protection regulations, and enhance trust with their customers. Don’t wait for a breach to occur—instead, take control of your data security today.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Enhancing E-Commerce Security with PCI DSS v4: the Role of Advanced Solutions like Jscrambler
This e-commerce security landscape presents a complex challenge: securing payment pages while complying with the PCI DSS requirements.
June 11, 2024 | By Jscrambler | 4 min read
Are my checkout forms filling attackers' shopping bags this holiday season?
E-skimming attacks have become attackers’ favorite strategy for stealing payment card data. All e-commerce companies are at risk. Why?
October 3, 2023 | By Jscrambler | 6 min read
