Jscrambler WPI 101 — Skimming Detection
May 27th, 2025 | By Jscrambler | 9 min read

Welcome back to the WPI blog series! Jscrambler WPI 101 is a series of articles about Jscrambler’s product Webpage Integrity (WPI), its main use cases, innovative features, and tips on maximizing the product's benefits.
This article focuses on the WPI use case for Skimming Detection and explains how Webpage Integrity enables you to protect your business against web skimming and data leakage.
The Dangers of Web Skimming
As web skimming attacks become more sophisticated, businesses face increasing pressure to secure their client-side environments, especially on sensitive pages like payment pages and login portals. Skimmers often operate silently, injecting malicious scripts into third-party code or exploiting weak points in the browser to siphon off personal and financial data without ever being detected.
To combat this, Jscrambler’s WPI Skimming Detection provides a proactive line of defense. Leveraging advanced static code analysis, it inspects every script running on your website, evaluating not just the code itself but how and where it executes. The system is designed to identify behaviors commonly associated with skimming, such as obfuscation, data encryption, unauthorized form injections, and access to sensitive information.
When a potential skimmer is detected, the Jscrambler platform offers detailed visibility into the threat, including which third-party vendors are involved and where the skimmer was found. This visibility empowers security teams to act quickly and precisely, removing the threat before any damage is done.
Preventing Digital Skimming with Jscrambler
The Jscrambler Skimming Detection engine aims to classify every individual third-party script present on a website and determine whether a potential skimmer is behind it.
The skimming detection capabilities within the Jscrambler dashboard are slightly different depending on whether you're using the full Webpage Integrity (WPI) product or a PCI DSS Module of the WPI. However, they pursue the same goal—helping you eliminate skimming risks to zero.
Inventory
A good way to get an instant overview of skimming threats is to check the Inventory in the WPI dashboard. The Inventory feature provides comprehensive visibility into all vendors and their scripts on the website, offering a better understanding of the various scripts in use. It allows users to identify the scripts' purpose, location, and impact on sessions and assess the associated level of risk based on verified actions and the potential types of threats they pose.
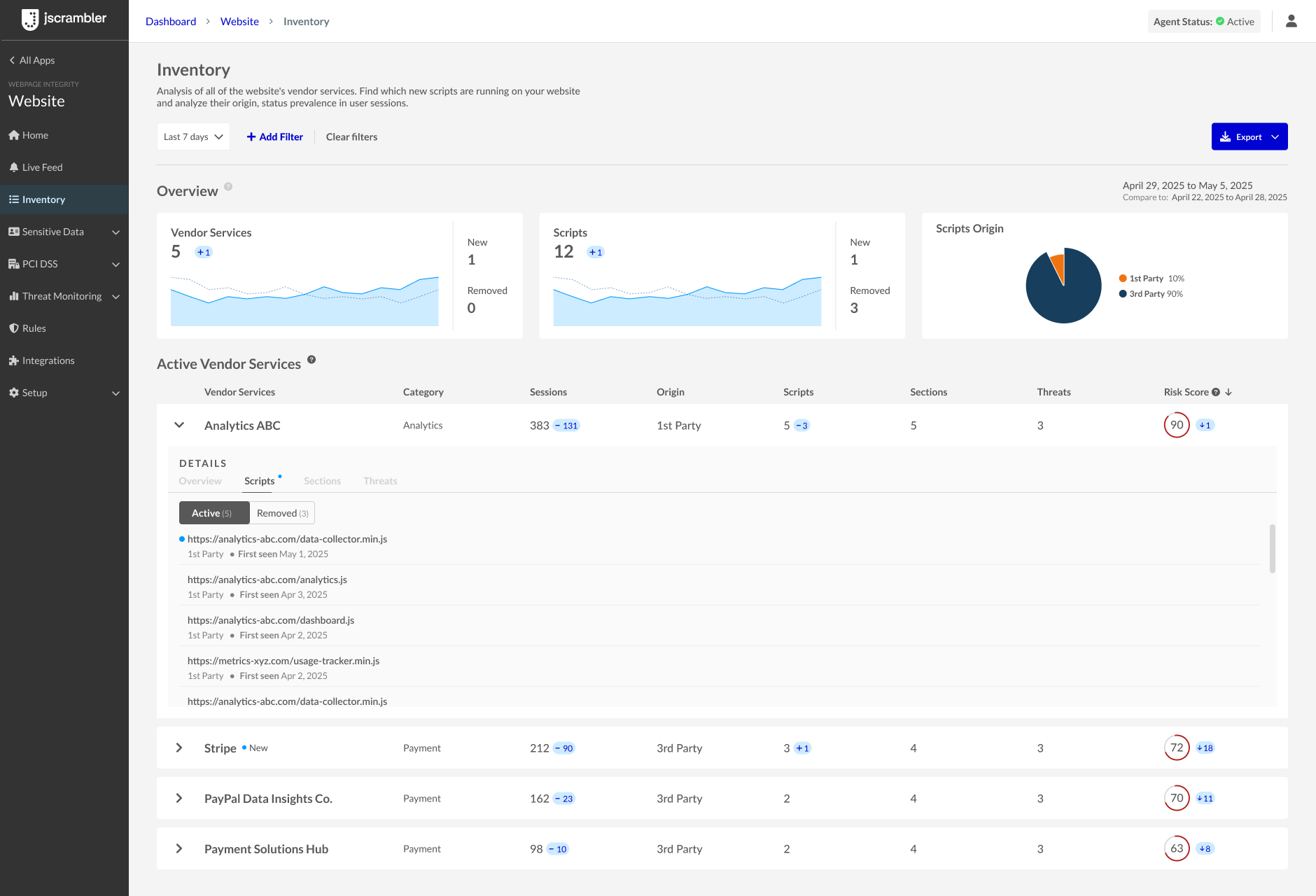 An example of an Inventory view with no skimming issues identified.
An example of an Inventory view with no skimming issues identified.
This goes beyond simply raising awareness of threats. The Inventory dashboard presents a qualitative measure that helps prioritize security actions and implement mitigation measures to address the impact of vendors present and active on the website.
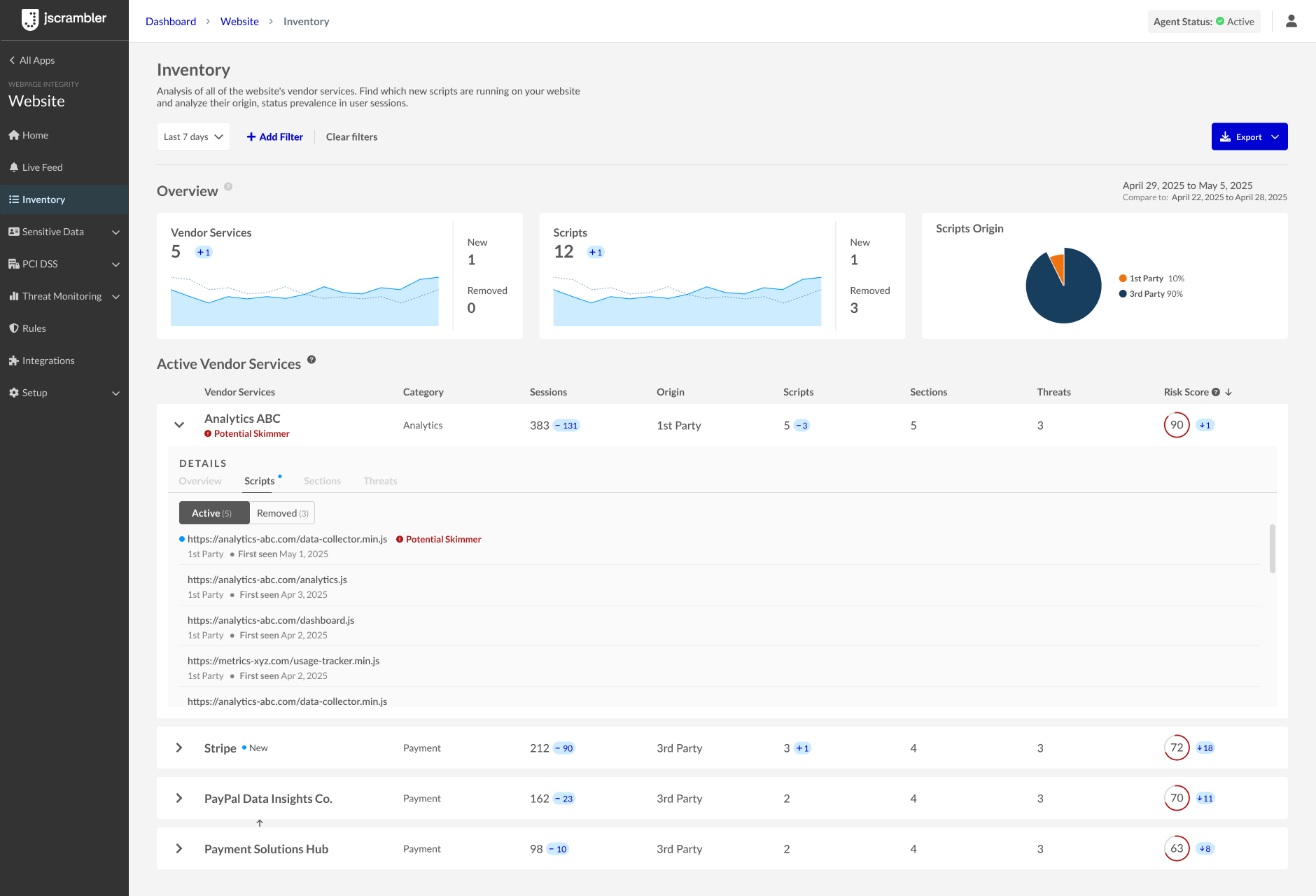 An example of an Inventory view with a potential skimmer identified.
An example of an Inventory view with a potential skimmer identified.
In addition, the Inventory feature provides visibility into threats related to sensitive data present or entered on the website. It enables verification of which scripts have access to specific data and ensures compliance with the appropriate data access permissions.
Skimming Detection
Now that you’ve spotted a skimmer in your Inventory view, what is behind it? You can go deeper to discover what happened and get more insight into the skimming risks. This is possible thanks to the Skimming Detection feature that is responsible for identifying and classifying scripts based on their potential security threats, including those associated with Magecart and skimming attacks. Skimming attacks are notorious for extracting sensitive information from websites, posing significant risks to both website owners and their users.
At its core, Skimming Detection is all about analyzing the scripts running on your website and flagging those that could be dangerous. Every script is scanned and categorized based on its behavior and the aspects detected in its code. If it looks clean, it’s marked as safe. But if it shows signs of malicious intent—especially those linked to Magecart-style skimming—it’s flagged as a threat.
This classification helps you stay ahead of attacks by giving you visibility into which scripts (and which vendors) could be putting your customers at risk.
Giving You Control: Manual Reclassification
Sometimes, a script might get flagged even when you know it’s safe. That's why we have built-in flexibility. If your technical team reviews a script and determines it’s not a threat, you can manually mark it as safe right from your dashboard. That change is reflected within minutes, ensuring your data stays current and actionable.
Vendors and Risk Scores
The Skimming Detection system doesn’t stop at individual scripts—it also looks at vendors. If a vendor has even one script flagged as Skimmer, the vendor itself gets tagged accordingly, and its risk score spikes to reflect that elevated threat level. Clean up the scripts, and the vendor’s risk profile improves. It’s that simple.
This system makes it easier to prioritize threats, monitor your third-party ecosystem, and protect your site from one of the web’s most dangerous types of attacks.
Skimming Detection for PCI DSS Compliance
The Skimming Detection section of the dashboard alerts merchants when skimming activity is detected in their vendor services. If no skimming is found, you'll see a reassuring message. If any skimming is detected, you'll be able to access a link that shows you which specific vendors are compromised.
By analyzing the behavior of web scripts and the context in which they execute, the system detects various indicators commonly associated with skimming activity, such as:
Stealth techniques
Data encryption
Injection of forms, iframes, and other elements
Access to sensitive data
Suspicious networking behavior
By evaluating these and other factors within the script and page context, the result provides a comprehensive assessment of whether potential skimming activity is present on the website.
If our system detects a potential skimmer—a malicious script designed to steal sensitive data, especially payment information—you’ll see it in the dashboard right away. You’ll see which vendors are involved and where exactly the threat was found, whether on a specific website or payment page. This visibility empowers your team to act quickly and precisely, minimizing risk and exposure.
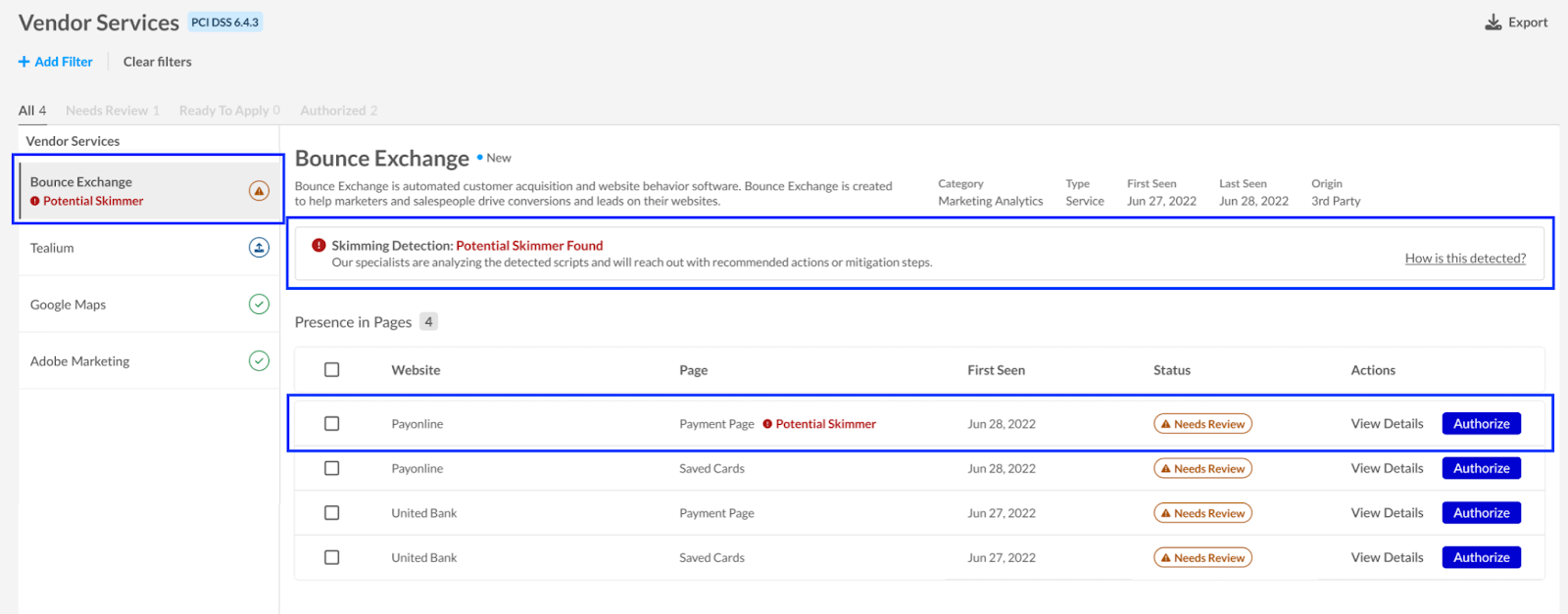
PCI DSS Module view with a “Potential skimmer found” notice.
No skimmers? No problem. When our system gives the all-clear, you’ll see a reassuring “No skimmer found” message. It’s peace of mind that your site is clean and your customers' data is safe, for now.
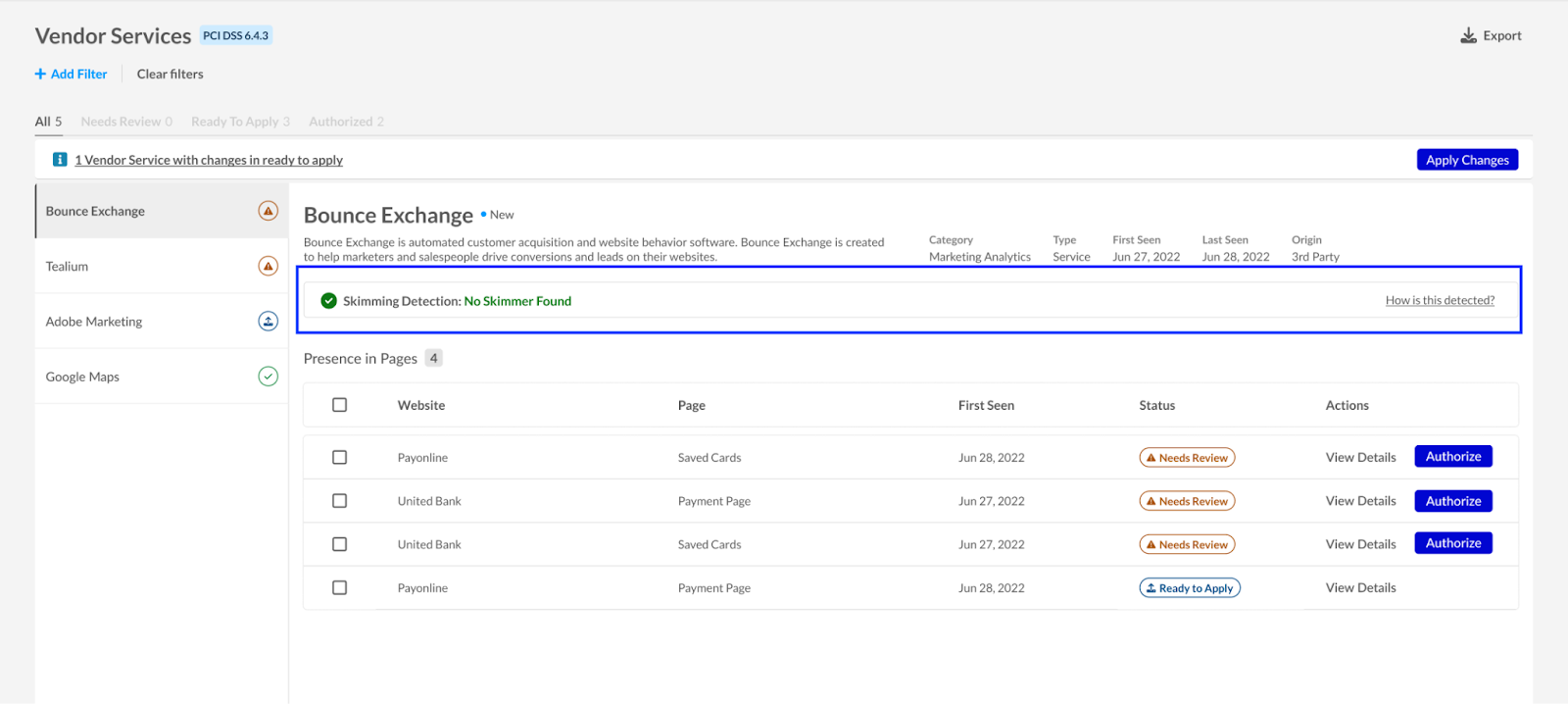 PCI DSS Module with a “No skimmer found” notice.
PCI DSS Module with a “No skimmer found” notice.
Next Steps After Skimming Detection
Jscrambler Webpage Integrity allows you to react to skimming alerts, review the malicious script or scripts in question, limit their access to data, and block them from performing malicious actions or data transfers.
In summary, the WPI product can block all unauthorized behaviors from third-party vendor scripts without preventing the script from loading on the page or performing authorized behaviors. This prevents actions such as skimming of payment, login, or other PII (Personally Identifiable Information) data, even if a vendor script contains both malicious code and useful code that is critical to the end-user experience.
As long as the script remains on the page, even if WPI is preventing all behaviors, it will still be included in the vendor inventory. The website administrator should remove a certain third-party vendor script to prevent its continued presence.
To learn more about the blocking capabilities of the Jscrambler WPI, check out the Form Fencing feature that specifically restricts third-party scripts from accessing form data. And stay tuned for the next WPI 101 series article that will cover PCI DSS compliance and how it helps meet the requirements 6.4.3 and 11.6.1, and goes beyond them with the blocking capability.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Digital Skimming: The Definitive Guide for 2025
Everything your business needs to know to counter the scourge of digital skimming and stay safe online.
December 24, 2024 | By Joyrene Thomas | 14 min read
Jscrambler WPI 101 - Form Fencing
Jscrambler WPI 101 is a series of articles about Jscrambler’s product Webpage Integrity (WPI), its main use cases, innovative features, and tips on how to maximize the product's benefits. This...
March 25, 2025 | By Jscrambler | 6 min read
