Leveraging Public Threat Intelligence for a Stronger Security Posture
March 30th, 2022 | By Adhyayan Panwar | 5 min read

Leveraging public threat intelligence improves organizations' security posture by enriching data into actionable intelligence to thwart cyberattacks.
We explore how organizations can use public threat intelligence frameworks like Alienvault OTX, MITRE, and others to enrich data into actionable intelligence to thwart future attacks.
Demystifying Threat Intelligence
Cyberattacks are at an all-time high. We hear about DDoS attacks, phishing campaigns, and malware campaigns daily.
To protect against these, organizations implement multiple protection layers, compounded with firewalls, antivirus software, monitoring systems, and many other available security solutions.
These security measures do their jobs, but some gaps always remain. This is where threat intelligence (sometimes called cyber threat intelligence, or CTI) comes into play.
What is Cyber Threat Intelligence?
In simple terms, threat intelligence is the collection of information and knowledge, private or public, regarding cyberattacks and associated threats.
Here is the fun part: these knowledge bases are very thorough. They contain data like origin and destination IPs, malicious domains, file hashes, and a lot of other technical data.
Alongside the technical data, threat intelligence also consists of abstract information about these attacks: attacking group movements in the past, using IOCs to figure out the APT behind the attack, predicting the next moves, etc. These are called tactics, techniques, and procedures, or TTPs.
You might be wondering what IOC, APT, and TTP, among others. Let’s look at frequently used terms when talking about threat intelligence.
Explaining the jargon
Let’s break down a few terms you will encounter while discussing threat intelligence. As we mentioned before, CTI is cyber threat intelligence, used as a collective term for all the actionable threat data.
Advanced Persistent Threats
Advanced Persistent Threats (APTs) are threat actors or a group of threat actors performing cyberattack campaigns at large scales.
Most APTs are nation-states or state-sponsored to some extent. As an example, a whole unit of the PLA (China’s army) is known as APT 1 (specifically PLA Unit 61398). Publicly available lists are present, containing extensive information about multiple APTs that is by no means exhaustive.
Indicator of Compromise
It is time to get technical now! IOC, or indicators of compromise, are pieces of technical information that were observed during a previously encountered attack.
If spotted within a system, they might suggest with a high degree of certainty that an intrusion has occurred. Multiple IOCs exist:
IP addresses
File hashes (MD5, SHA1, etc)
Malicious domains
Crypto wallets associated with known miners
Phishing emails, etc.
Practical example
In an attack a few months ago, traffic from the infected machine was seen toward IP 1.2.3.4. This could be a beacon, data exfiltration, or anything else.
Now say you find the same IP, i.e., 1.2.3.4, as the destination address in recent traffic logs. There is a big chance the server is compromised, and you can now take action against it. But there is a caveat with IOCs: they emerge after the attack occurs.
Bad actors can spawn new IPs, register new domains, or change a variable in the source code of a binary, which can result in new file hashes!
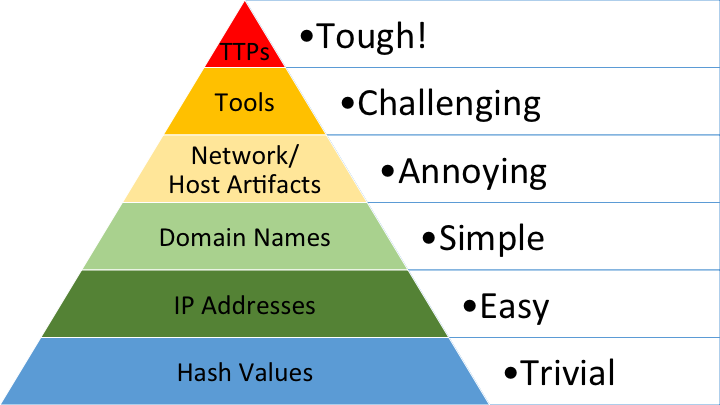
The Pyramid of Pain, introduced by David Bianco, explains how much pain each type of IOC might cause adversaries while protecting against them.
That’s where TTPs come into play: tactics, techniques, and procedures (or TTPs) are abstract information about the way APTs carry out their attacks. In essence, TTPs reflect their modus operandi.
Sometimes, TTPs are considered a type of IOC (as shown in the Pyramid of Pain). They are strongly guarded confidential information kept by security vendors like Mandiant, Recorded Future, etc.
TTPs are also considered better protective measures than IOCs because attackers might easily evade IOCs to bypass TTPs. However, a complete overhaul of the existing methodology is required, which, more often than not, is not feasible.
TTPs are greatly sought after by attackers to gain insight into how much is known about their techniques. This was the case in the popular SolarWinds supply chain attack campaign more than a year ago, where UNC2452 (the APT behind the attacks) made sure to get their hands on the TTPs collected about them when they breached FireEye.
How can CTI be leveraged?
CTI in action
Leveraging cyber threat intelligence and deploying it for protective measures could prove crucial while battling against cyber attacks. The majority of cyberattacks go undetected, but proper usage of CTI might prevent that.
Talking about threat intelligence is incomplete without bringing the MITRE Corporation into the conversation.
The MITRE Corporation is a non-profit organization that helps companies worldwide fight cybercrimes by providing a curated and collated collection of threat intelligence in the form of their ATT&CK framework.
The ATT&CK framework has multiple techniques that are part of an attack, with categorization and sub-techniques to provide more granularity.
If you want to know which APT uses which specific tool to perform an action, ATT&CK will have your answer. They introduced the D3FEND framework and matrix, which are more focused on defensive operations, highlighting techniques that can be used to protect systems.
Other open-source players in CTI also exist, like Alienvault OTX, AbuseIPDB, ThreatMiner, and many more. These IOCs are confirmed to have been a part of an attack or known malicious activity in the past.
Plug these feeds into your onsite SIEM and SOAR tools, coupled with MITRE techniques for classification of threat intel generated within your organization, and you will end up with CTI put effectively to work and thwarting attacks!
Conclusion
There is no denying that security products do a great job of minimizing the risk of cyberattacks, but they are not enough.
To further minimize the gaps in the security posture, it's also necessary to use a mixture of reactive (IOC) and proactive (TTPs) cyber threat intelligence.
It’s also important to note that sharing threat intelligence information with the security community is a critical step in collectively leveraging knowledge and experience to understand threats.
Lastly, CTI is a broad topic that goes beyond the scope of this blog article, but we hope that we made you curious enough to explore this interesting field and use it to secure your assets.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Interview with Andrzej Mazur - Game Development Using JavaScript
The first in our series of interviews is with Andrzej Mazur, js13kGames competition creator and HTML5 Game Developer, talking about the perks and benefits of using JavaScript on game development.
September 8, 2017 | By Jscrambler | 7 min read
Open Source Components and a Push for In-Depth Security
In this article, Pedro Fortuna provides his take on the recent debate about the security of using open source components. Can agility and security coexist?
December 14, 2018 | By Pedro Fortuna | 3 min read
