Protect Your Online Privacy: Everyday Practical Tips
September 23rd, 2025 | By Ezekiel Lawson | 15 min read

Most of us use the internet without considering what we’re sharing. A quick search here, a new app there, it all adds up. Then one day, you notice a strange ad or get a message that doesn’t feel right, and you wonder how your information got out. Situations like this are now part of everyday life. Online privacy isn’t just a tech issue. It affects everyone. The things we do or share, often without thinking, can be used to profile us, influence what we see, or even steal our identities.
But you don’t need to feel helpless. With a few simple steps, you can take back control and protect your information. This guide walks you through practical actions to strengthen your privacy. No technical skills are needed. Whether you’re using a phone, tablet, or computer, you’ll find clear tips to help you stay secure.
What does Online Privacy Mean?
Online privacy means having control over your personal information; what is shared, who sees it, and how it’s used. However, with so much of our lives happening online, that control can slip away quickly and unknowingly.
Consider this:
You install a weather app, and it asks for your location, even when you're not using it. You search for a pair of shoes once, and ads for that brand follow you around for days. You take a quiz on social media and unknowingly share details like your birthday, hometown, and interests.
These actions might seem harmless, but they create a digital trail—a profile of who you are, what you like, and where you go. That data is often collected, stored, and shared or sold by the apps and websites you use.
Why Privacy and Security Go Hand in Hand
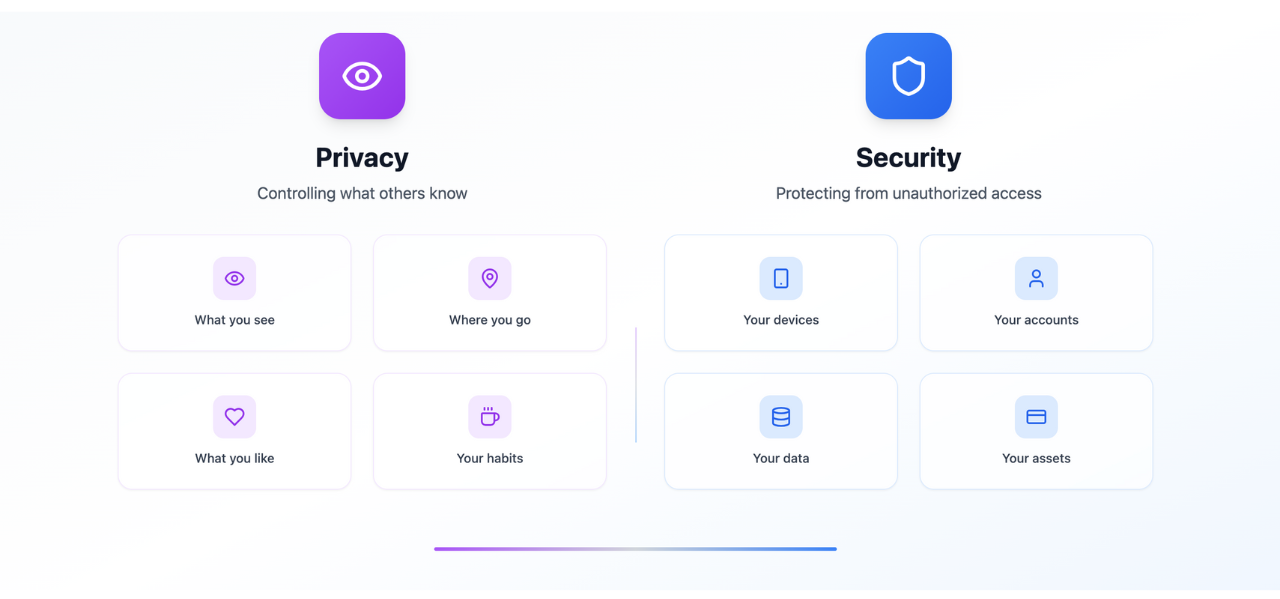
Privacy and security work together, but they aren’t the same.
Privacy is about controlling what others know about you: your habits, location, preferences, and more.
Security is about protecting your devices, accounts, and information from unauthorized access.
You may have strong security measures, such as two-factor authentication, but still share personal details or grant app permissions that compromise your privacy. True online safety means paying attention to both. To make things more practical, let’s start with one of the most common and overlooked habits that can quietly put your privacy at risk.
1. Limit exposure of personally identifiable information (PII)
We often share more about ourselves online than we realize. A birthday post, tagged location, or visible phone number might seem harmless, but when combined, these details can paint a complete picture of your identity. Cybercriminals do not need much. With just a few facts, such as your date of birth, address, or workplace, they can answer security questions, impersonate you, or launch targeted scams.
For example, posting your full name and birthdate on Instagram might seem harmless. However, if that information is public and your LinkedIn profile lists your job history, a scammer could use those details to craft realistic phishing emails.
If you are unsure what qualifies as personal data, look into this article on Personal Identifiable Information. It clearly outlines what types of data are considered sensitive and how each one can impact your privacy and security.
Actionable steps:
Avoid posting your exact birth date, home address, or phone number publicly.
Review the privacy settings on your social media accounts.
Use aliases or abbreviations when signing up for non-essential platforms.
Refrain from engaging in social media quizzes or posts asking personal questions; they’re often used to mine data for attacks.
2. Choose privacy-focused web browsers
Most people don’t realize that their web browser may be collecting and sharing data about everything they do online. Popular browsers often track your browsing history, location, and search behavior to feed advertising algorithms. This means your personal interests, habits, and even medical or financial research can be recorded and shared with third parties.
Imagine searching for information about a medical condition or financial planning. A few days later, you start seeing targeted ads related to that topic on different platforms. That’s not a coincidence; it’s your browser sharing what you search with ad networks.
Actionable steps:
Regularly clear your browsing data if needed and block third-party cookies.
Switch to browsers that prioritize privacy, such as Brave, Mozilla Firefox, or the Tor Browser.
Brave Browser
Brave is a secure and trusted browser that automatically blocks trackers and ads, providing a faster and more private browsing experience.
Firefox
Firefox is a reliable browser that puts privacy first by blocking pop-ups and protecting against spyware, although it may not be the fastest.
Tor Browser
Tor is built for anonymous browsing and routes your traffic through multiple servers worldwide to keep your activity private and untraceable.
3. Log out of shared or public devices immediately
Using a shared or public device, such as a friend’s laptop, a school computer, or one in a hotel lobby, may be convenient at the moment, but it comes with serious privacy risks. If you forget to log out, the next person to use that device could easily access your personal information, like emails, cloud files, or even bank accounts, without needing your password.
You might check your email on a friend’s laptop and forget to sign out. Later, someone else uses the same browser and accidentally gains access to your open session. Simple oversights like this can lead to unintentional data exposure.
Actionable steps:
Always log out of your accounts once you're done. It only takes a few seconds, but it can save you from a serious privacy breach.
Use Incognito or Private Mode if you need to access personal information on someone else's device. This helps ensure your session details aren’t saved.
Try not to get too comfortable. It’s easy to click “Remember me” or “Stay signed in” out of habit, especially when you’re in a rush or you are used to that option on your device.
If you think you may have left a session open, log in from your device and check your account’s active sessions. Most platforms allow you to remotely log out from all devices with a single click.
4. Disable unnecessary notifications and pop-ups
Pop-ups and random push notifications might seem like harmless distractions, but some are far more than just annoying; they’re designed to trick you. That unexpected alert promising a free phone or gift card could lead you to a fake website built to steal your personal information. All it takes is one accidental click.
What makes these tricks effective is that they play on our emotions. We get excited at the idea of winning something for free, and in that moment, we don’t stop to question it. But let’s be honest, how can you win a phone or gift card you never applied for? Scammers are aware of this and exploit it to their advantage. Recognizing these offers as fake is the first step to staying safe.
Actionable steps:
Go to your browser settings and block pop-ups to reduce exposure to unwanted ads or malicious links.
Allow notifications only from apps you use frequently and trust, such as messaging or banking apps.
Review your notification permissions on both mobile and desktop, and remove access from apps that no longer serve a clear purpose or that you do not recognize.
5. Watch out for AI-generated phishing scams
Phishing attacks have become significantly more sophisticated than they were in the past. In the past, it was easier to spot a fake message due to poor grammar, unusual formatting, or suspicious links. However, phishing has evolved; scammers now utilize advanced AI tools to craft realistic emails, clone entire websites, and even mimic the voices of real people through deepfake audio.
.png)
The emails look official, with correct logos and sender addresses that seem legitimate. Their goal is to create a sense of urgency so that you will click on a “dispute” or “cancel order” link without thinking. These scams are becoming increasingly common and sophisticated, making them more challenging to spot. A phishing email might look exactly like a real message from your bank, a delivery service, or even your employer. Some attackers now use AI chatbots to pose as customer support agents, keeping you on the line just long enough to collect sensitive data.
Actionable steps:
Be cautious with any unexpected communication. If you receive a message that asks you to click a link, download an attachment, or confirm personal details, even if it appears to come from a trusted source, pause and verify it first.
Use link checkers like VirusTotal, PhishTank, or Google Safe Browsing to inspect URLs before clicking them.
Double-check sender information. Hover over email addresses and links to see where they lead. Scammers often use addresses that look very close to legitimate ones but include subtle differences.
Never give sensitive information over the phone or by email unless you initiated the conversation. If you’re unsure, end the call or ignore the email and contact the organization directly through their official website or customer support.
6. Conduct regular checks on your online profile
You might be surprised at what’s visible about you online. Old blog comments, forgotten photos, or outdated information can show up in search results, and some of it may not reflect who you are today. For instance, if a potential employer searches your name and finds a 10-year-old comment or photo that doesn’t align with your current values or image. This could impact your opportunities without you even being aware of it.
Take a few minutes now and then to search your name, email address, or social media usernames on search engines like Google, Bing, or DuckDuckGo. Knowing what others can find about you online gives you a chance to clean up what doesn’t belong or no longer serves you.
7. Use public Wi‑Fi with caution
The joy of having access to free internet has made public Wi‑Fi a trusted companion in our daily routines. Maybe you have quickly connected at the airport to check your flight status, uploaded a document from a café while sipping coffee, or replied to work emails in a hotel lobby. It feels like a small win; free, fast, and easy.
But that convenience often hides real risks. What seems like a harmless connection could quietly expose your details. Most public networks are usually unprotected, making it easier for hackers to spy on your activity or install malware on your device.
Conclusion
While the steps shared in this article cover some of the most common ways users put their privacy at risk, it’s only the beginning. Online privacy is a broad and constantly evolving topic, but understanding how your data can be exposed is the first step toward protecting it. You don’t need to change everything overnight; start with minor changes. Simple actions, such as switching to a more secure browser, logging out of shared devices, or reviewing your online profiles, can have a significant impact.
Choose one step that feels manageable and build from there. Over time, protecting your privacy won’t feel like an extra task; it will become second nature in how you use the internet every day.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Data Privacy in Financial Services: Why and How?
In a bid to remain competitive, and meet evolving customer expectations traditional brick-and-mortar financial services have given way to online banking, mobile apps, and contactless payments –...
August 27, 2024 | By Tom Vicary | 11 min read
18 Cybersecurity and Hacker Movies and Series to Watch
The top 18 cybersecurity and hacker movies and series list is a curated selection by our team. If you are in the mood for hearts pumping, a good movie about hacking never disappoints.
November 28, 2023 | By Jscrambler | 13 min read
