The Problem of Exposed Code in Healthcare Apps
July 14th, 2020 | By Jscrambler | 3 min read

The problem of exposed code in Healthcare apps comes up with the digitalization of healthcare services. It has prompted companies to release Web and mobile platforms that allow consumers to easily access a myriad of services.
However, as positive as this shift has been for companies and consumers alike, it means that extremely sensitive data, such as Protected Health Information (PHI), is now more exposed to cyberattacks.
In 2019, 33 million patients had their PHI breached or stolen, and many of them faced identity theft and fraud. Companies also incur significant costs in attack clean-up, compensations to clients, and loss of revenue due to negative press.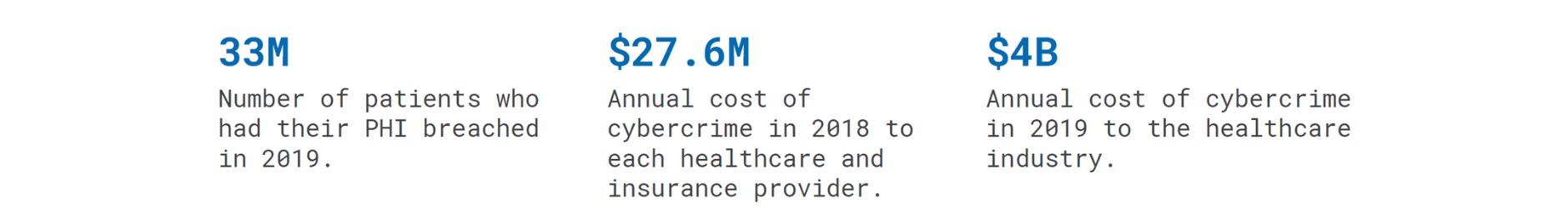
Contact Tracing Apps
One very specific case of healthcare applications that has surfaced recently is contact tracing apps. These apps are being developed all over the world as a response to the COVID-19 pandemic.
In a nutshell, a contact tracing app allows people to be notified whenever someone that they were in close contact with tested positive for COVID-19 (provided that both were using the app).
The use of these apps has been surrounded by fear and controversy, especially because they handle such sensitive information. But beyond this complicated question of data privacy, there's the matter of security.
With thousands of security vulnerabilities for attackers to exploit as well as integrity-related weaknesses that can be abused, the teams behind contact tracing apps need to put strict application security in place.
And even though only a few contact tracing apps have been released, we have already seen critical security incidents.
Scam Copycat Apps
In June 2020, security researchers found 12 fake contact tracing apps targeting citizens in Asia, Europe, and South America. These apps are copycats of official government apps, using their actual branding to trick users into trusting them.
When users install these scam apps, they covertly install malware on the device, including banking trojans that steal user credentials and personal data. Apart from financial fraud, victims can become targets of ransomware and identity theft.
These so-called low-tech attacks are based on attackers retrieving the source code of the legitimate app and deploying it somewhere else. Then, attackers distribute them using unofficial app stores and third-party apps.
Data Exfiltration
While scam copycat apps pose a significant threat, a more serious concern in healthcare applications (including contact tracing apps) is data exfiltration.
By default, once deployed, applications lack any type of integrity verification controls, and their source code is left completely exposed and unprotected.
As stated in the OWASP Mobile Top 10 project, this allows attackers to "reveal information about back-end servers; reveal cryptographic constants and ciphers; steal intellectual property; perform attacks against back-end systems; or gain the intelligence needed to perform subsequent code modification".
By understanding how the application works, attackers get one step closer to planning/automating data exfiltration or scraping attacks.
How to Protect Healthcare Apps
With the stakes being this high in healthcare and government-backed apps, security teams must go the extra mile to ensure that attackers remain locked out.
Using current technology, the security teams behind these implementations can (and should) add protective layers to these apps’ source code. One key layer is obfuscation, a technique that transforms the source code into a new version that is extremely hard to reverse-engineer.
Another important security layer is code locks. These tie the source code to a list of allowed environments and Operating Systems and break the app when it is run outside of this list. By locking attackers out, this security layer goes a long way toward preventing low-tech copycats and scam apps.
Finally, runtime defenses must be present as an additional layer of security.
These can be set up to break app execution when there has been any type of compromise to the integrity of the app. So, whenever attackers try to debug the app or change its source code, the app will immediately break, on purpose, and make attackers lose their progress.
Final Thoughts
In times of fast digitalization, application security can't lag behind.
Every year, attackers manage to get hold of the protected health information of millions of patients. With contact tracing apps making their debut, we're already seeing critical security incidents that originate from unprotected source code.
Healthcare organizations must act fast to put in place vetted security systems and ensure that the source code of their apps won't serve as a gateway to data exfiltration attacks.
We present several case studies about protecting code, namely one showing how a healthcare company has used Jscrambler to harden the source code of its apps and increase its compliance with data privacy regulations.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
JavaScript Obfuscation: The Definitive Guide for 2026
JavaScript obfuscation is a series of code transformations that make JS extremely hard to understand and reverse-engineer. This definitive guide explores it in-depth.
January 13, 2026 | By Jscrambler | 18 min read
12 Useful JavaScript Newsletters
With so much happening in the JavaScript ecosystem, it's not easy to stay on top of things. Here are 12 newsletters to bring the best news straight to your inbox.
August 5, 2025 | By Abigail Amadi | 10 min read
