[Case Study] Preventing Automated Abuse with Arkose Labs and Jscrambler
November 6th, 2018 | By Jscrambler | 4 min read
![[Case Study] Preventing Automated Abuse with Arkose Labs and Jscrambler width=](/img/containers/images/jscrambler-blog-preventing-automated-abuse-arkose-labs-jscrambler.jpg/1dfd36572b0d87d43596ba05fa824fba.webp)
Jscrambler's resilient client-side protection solution unlocks new technological breakthroughs for several businesses across different sectors, preventing automated abuse, among other vulnerabilities and attacks.
We will explore how Arkose Labs has been leveraging Jscrambler's technology to deliver the most advanced automated abuse prevention solution, which is resilient to abuse and tampering.
Today, more and more security verification needs to be done on the client-side.
The Importance of Bot Detection
The distinction between human and bot actors has been a concern since the Internet's early days.
Since its inception in 1997, CAPTCHA has become a widespread technology for helping to prevent automated online abuse by hackers and spammers.
In the modern digital landscape, new and highly sophisticated security problems arise, given the prevalence of automated attacks. The most frequent forms of automated abuse include:
Account Takeovers: injection of breached credential pairs to fraudulently access user accounts;
Fake Users: bulk account creation by misusing and automating sign-up processes;
Spam: distribution of malicious/untrustworthy information in public content, databases, or private messages;
Carding: multiple payment authorization attempts that verify the validity of stolen gift card data and exploit their value;
Blocking Transactions: automated product stock reduction techniques without transactions to deny inventory for other users;
Fake Ratings: artificial inflation of public endorsements and skewing credibility to influence users or undermine reputation;
Scraping: automatic extraction of valuable content from websites and unauthorized distribution for financial gain.
Enterprise companies have become appealing targets for these automated attacks. With this need for increased security, Arkose Labs brings a leading bot mitigation technology.
Arkose Labs' Technology
Mitigation-focused strategies that use threat scoring and behavioral analysis are not enough to overcome automated abuse.
Arkose Labs uses a bilateral approach that combines its global telemetry with a patent-pending enforcement challenge.
The global telemetry recognizes users across their entire network with an anonymous alphanumeric identifier, which builds a dynamic score that qualifies their risk profile and reputational integrity.
Unrecognized suspicious users go through an enforcement challenge to authenticate their identity and validate the telemetry.
The patent-pending enforcement challenge draws upon millions of security images, orchestrated in real-time from three-dimensional models, to present interactive visual subjects generated uniquely for that user.
This forces attackers to engage expensive counsel on machine vision and machine learning to bypass the challenge at scale — rendering attacks uneconomical.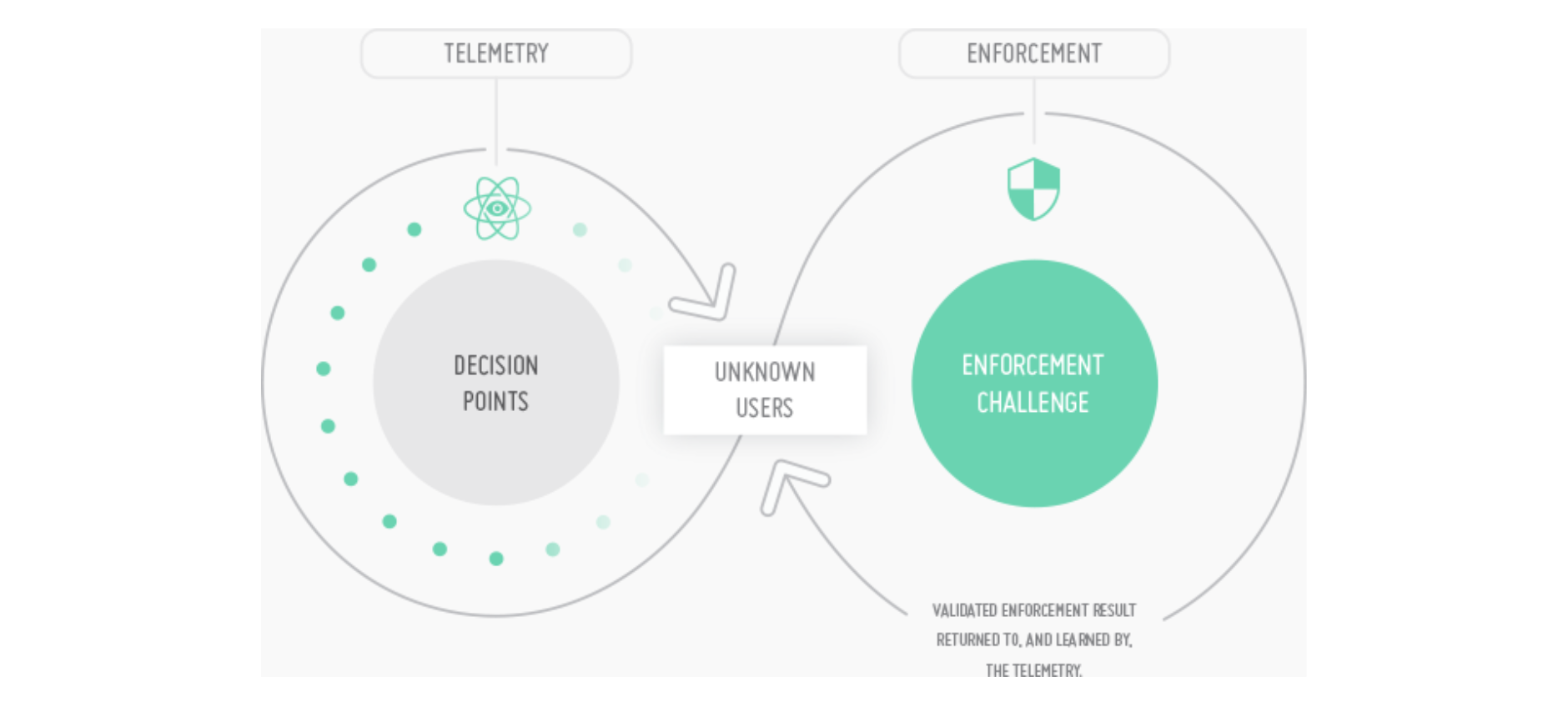 This bilateral approach trains the Arkose Labs telemetry against serving enforcement to legitimate human users — which means no false positives and zero friction to users.
This bilateral approach trains the Arkose Labs telemetry against serving enforcement to legitimate human users — which means no false positives and zero friction to users.
Most importantly, it removes the economic window necessary to commercialize fraud through Brute Force, Sweatshops, Machine Vision, and Single Request Attacks.
Single Request Attacks are specifically relevant, as they facilitate the most advanced automated abuse seen today.
Each request is commonly made by a headless browser, executes JavaScript like a legitimate human user, and presents a dynamic client/network fingerprint to conceal the origin. This systematic approach can decouple tell tales and obscure critical security breaches.
While it bypasses all other bot mitigation products, Arkose Labs’ patent-pending solution successfully stops them.
Jscrambler for a Tamper-Proof Solution
In recent years, we've seen cases of automated abuse technologies being reverse-engineered for malicious purposes. Reverse engineering grants attackers a way to circumvent security systems and perform devastating automated attacks.
This is precisely what happened to Google's reCAPTCHA in 2014. Its code was obfuscated by Google's own obfuscation techniques but, because it was static and followed a certain obfuscation pattern, it was reverse-engineered a few days after release, opening the door to automated bypass.
Arkose Labs leverages Jscrambler's leading code protection solution to obfuscate and conceal the logic of its own technology. As so, its technology becomes tamper-proof with the highest level of resilience.
On top of this, Arkose Labs also leverages more advanced protection features that are employed as needed. These advanced features include code locks (preventing the code from running outside a set of allowlisted domains, browsers, dates, and OS'es) and self-defending capabilities.
"We have keys that we encrypt into the client and then the API itself changes. So, when we turn this mode on, if you don't correctly render our JavaScript and can't correctly go through and render our technology in a real browser on one of our customers' websites, the API will deny the input. This is what we can achieve with Jscrambler." — Kevin Gosschalk, Arkose Labs' CEO.
With these advanced Jscrambler protection features, Arkose Labs prevents attackers from using simplistic headless browsers such as cURL to bypass their enforcement technology. By closing these client-side doors to exploits, the cost of attacks is driven up to a point where attackers are more likely to give up.
Jscrambler's client-side protections are then able to increase the security of Arkose Labs' technology without changing it or resulting in harder enforcement challenges. Instead, it enforces a secure environment where Arkose Labs' technology is run.
Arkose Labs also gives their code a unique distinction: polymorphic behavior.
By running Jscrambler in their build process, each new Arkose Labs build presents an entirely different code, while keeping the same functionality. As a result, the keys also change — once again driving up the cost of attacks and rendering them uneconomical.
Bottom-line Results
After nearly two years of using Jscrambler's technology, no attacker has been able to reverse-engineer Arkose Labs' code, even in highly sophisticated attack scenarios.
In the recent joint Webinar with Jscrambler and Arkose Labs, Arkose Labs' CEO Kevin Gosschalk shared his thoughts on the importance of leveraging client-side security: "Using Jscrambler in your defense playbook is highly effective".
Consider Arkose Labs to prevent automated fraud and abuse in your business. If you're interested in learning how Jscrambler can protect your Web applications, request a demo or get in touch with us.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Preventing Digital Skimming Attacks and Enabling PCI DSS Compliance
E-commerce skimming = the majority of attacks against payment card data. The newest version of PCI DSS contains requirements aimed at preventing digital skimming attacks.
June 21, 2022 | By John Elliott | 5 min read
Preventing Intellectual Property Theft with Jscrambler
In this post, we explore what is intellectual property theft, its consequences, and how to prevent it with Jscrambler.
October 8, 2021 | By Jscrambler | 6 min read
How To Automate PostgreSQL and repmgr on Vagrant
In this tutorial, we build a fault-tolerant PostgreSQL cluster using Vagrant and Ansible. This configuration may help minimize deployment issues.
July 28, 2020 | By Rui Trigo | 9 min read
