Preventing Intellectual Property Theft with Jscrambler
October 8th, 2021 | By Jscrambler | 6 min read

Prevent intellectual property theft with Jscrambler. How and why is it important to be protected against intellectual property theft?
Intellectual property theft (also called IP theft) refers to someone illegitimately taking possession of someone else’s proprietary inventions or developments.
In the context of business, and specifically in IT, IP theft refers to a competitor or malicious actor getting access to trade secrets or proprietary algorithms to be used to the thief's own advantage.
The acceleration of digital transformation has stimulated the development of new technologies, increasing the value of companies' intellectual property. This creates new opportunities for attackers and scammers.
We have witnessed copycat apps going rampant in app stores, stealing business away from original developers, and fake COVID tracking apps mimicking official government apps and installing malware on the user’s device.
Most intellectual property theft occurs in countries with ambiguous IP laws, which makes enforcement difficult. But even though tackling this problem is no easy task, prevention is more beneficial for businesses than remediation.
Consequences of Intellectual Property Theft
The Commission on the Theft of American Intellectual Property points out in their IP commission Report that IP theft ends up costing affected companies around $225 billion to $600 billion. While this figure will vary from case to case and the indirect damages are difficult to estimate, it’s enough to understand the potential damages in specific examples.
Copycat Applications
In copycat applications, malicious actors steal the whole source code of the application and deploy it posing as a legitimate app. They may then monetize the application, taking advantage of the leniency that app stores are displaying, failing to crack down on copycats.
There’s a direct impact on the affected business from the loss of revenue.
The vast majority of users aren't able to differentiate between an original app and a copycat, and so while the original app remains available in app stores (which can go on for months), the copycat app will be diverting sales. In some cases, the copycat app can also be used to distribute malware, jeopardizing the reputation of the company.
Proprietary Algorithm
A second example of IP theft relates to a competitor wanting to retrieve a proprietary algorithm.
In highly competitive sectors such as E-Commerce, companies invest in specialized algorithms to improve their conversion rate.
Competitors may go through the app’s source code to analyze the logic of these algorithms, allowing them to mimic their behavior and utilize it for their own gain.
As a result, the company that originally developed the algorithm will lose a competitive advantage that could translate into millions of dollars in revenue.
How to prevent intellectual property theft with Jscrambler
To prevent intellectual property theft in web and mobile applications, businesses need to adopt adequate measures to secure their intellectual property (i.e., their source code). But how can they secure it?
To make this easier to digest, let’s pick up our previous two examples: copycat applications and a competitor trying to retrieve a proprietary algorithm.
Tip: For a hands-on experience, feel free to try the code protection measures we will explore below on your code by using a Jscrambler free trial.
Stopping Copycat Applications
Malicious actors will try to get access to the source code of the original application to copy it and benefit from it.
To prevent that, businesses need to focus on adding strong protection to their source code to stop those malicious actors from ever being able to understand or replicate the code’s logic.
The answer to this is to apply code obfuscation along with other code protection techniques that can be used to stop third parties from trying to reuse the code. This is a security recommendation from OWASP.
Step-by-step: JavaScript Obfuscation
Conceal the code using JavaScript obfuscation, which includes a series of code transformations that turn the otherwise exposed code into a protected version that is extremely hard to understand and reverse-engineer.
To make the concealed code effectively safe from copycats, obfuscation alone isn't enough. An obfuscated app will run just like the original code, so copycats could just replicate that code. Simple obfuscation tools fail the purpose of actually making it hard for copycats to create app replicas.
Jscrambler provides copycat protection by applying additional strong code protection techniques on top of the obfuscation, namely Code Locks and the Self-Defending layer.
Step-by-step: Code Locks
Code Locks are useful against copycats because they provide control over the environment in which the code is allowed to run.
A date lock, for example, automatically expires the code after a certain time, meaning that copycats would have to continuously retrieve fresh batches of code to avoid having broken apps.
A browser or domain lock, on the other hand, allows the locking of the original code to certain browsers or domains, which prevents the copycat from actually running.
In case the copycats attempt debugging the code to try and learn how the application works, Jscrambler’s Self-Defending feature protects functions and object literals, concealing their logic, and detects debuggers to trigger defenses that thwart reverse engineering attempts.
Stopping Competitors from Retrieving a Proprietary Algorithm
When it comes to valuable proprietary algorithms, competitors may want to try and retrieve the source code that contains them to use them to their own advantage.
To prevent that, we need to protect the source code.
Let’s take a look at the example code below. It’s an algorithm that recommends products based on the customer’s previous purchase history.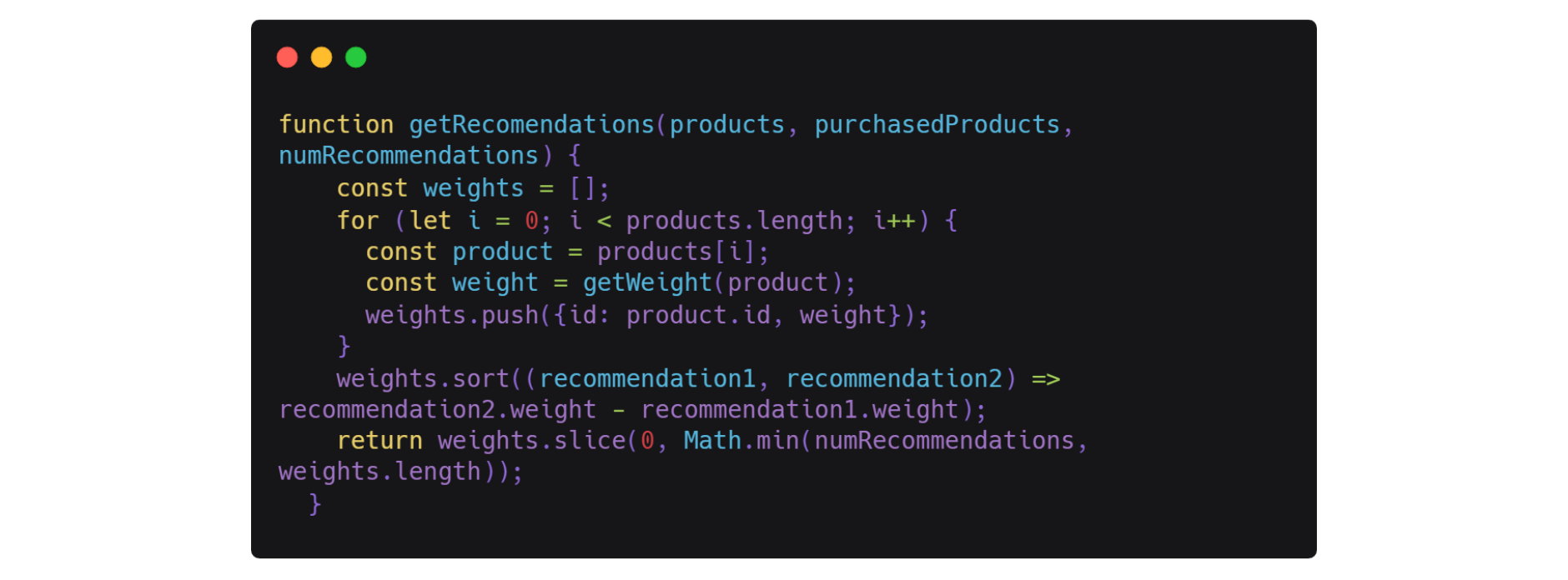
Now, if this were a proprietary algorithm, naturally, we would not want to leave that code exposed to our competitors. Simply by analyzing this code, they could potentially replicate the algorithm altogether. So, our first step would be to conceal all this logic with JavaScript obfuscation, taking advantage of Jscrambler’s several transformations.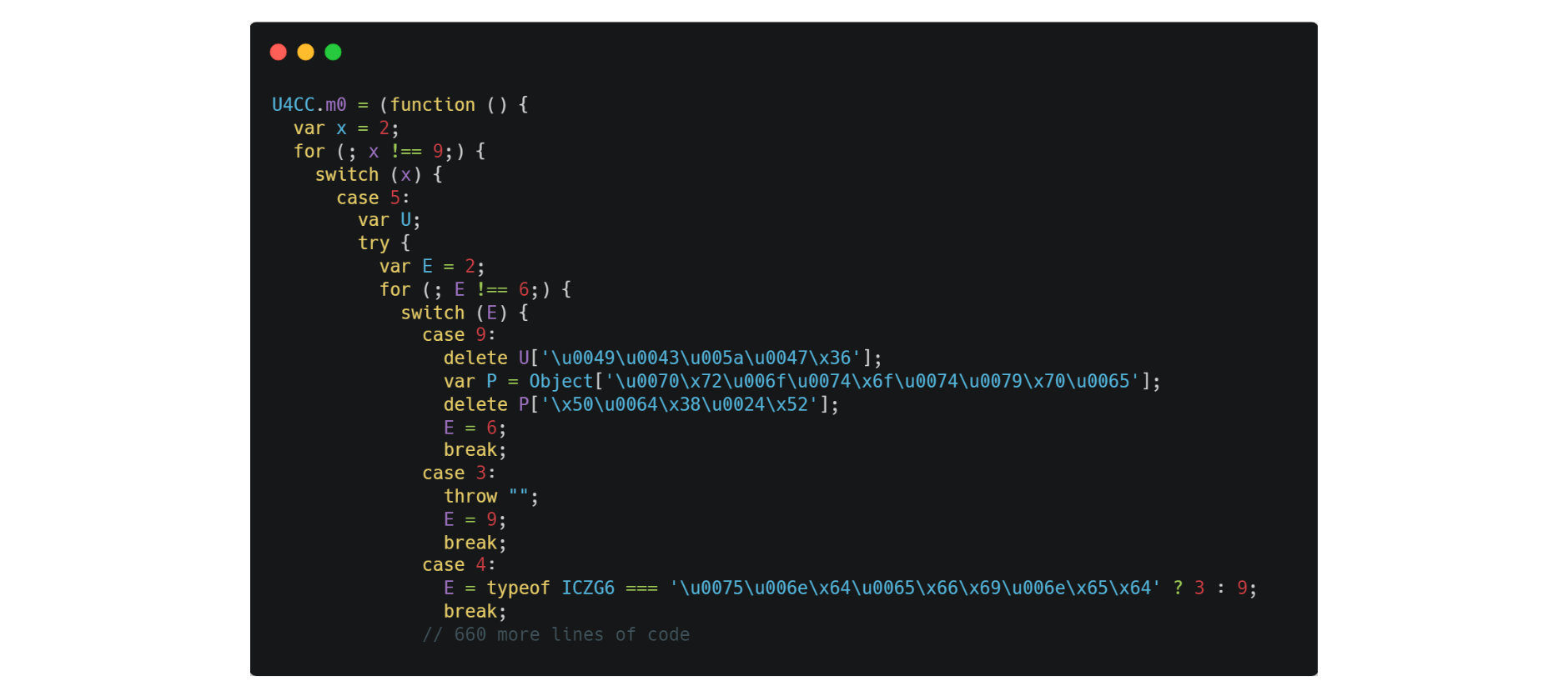
In the code snippet above, we can see the results of using Jscrambler’s Control Flow Flattening transformation. It flattens the flow of the program by removing the natural conditional constructs that make the code easier to read.
As a result of this single transformation, the code is already extremely hard to understand and reverse-engineer.
Applying a single transformation would not be enough to fully protect the code from competitors’ eyes. The Control Flow Flattening transformation used above doesn’t change any of the names, numbers, or strings that were used in the original algorithm, as we can see below.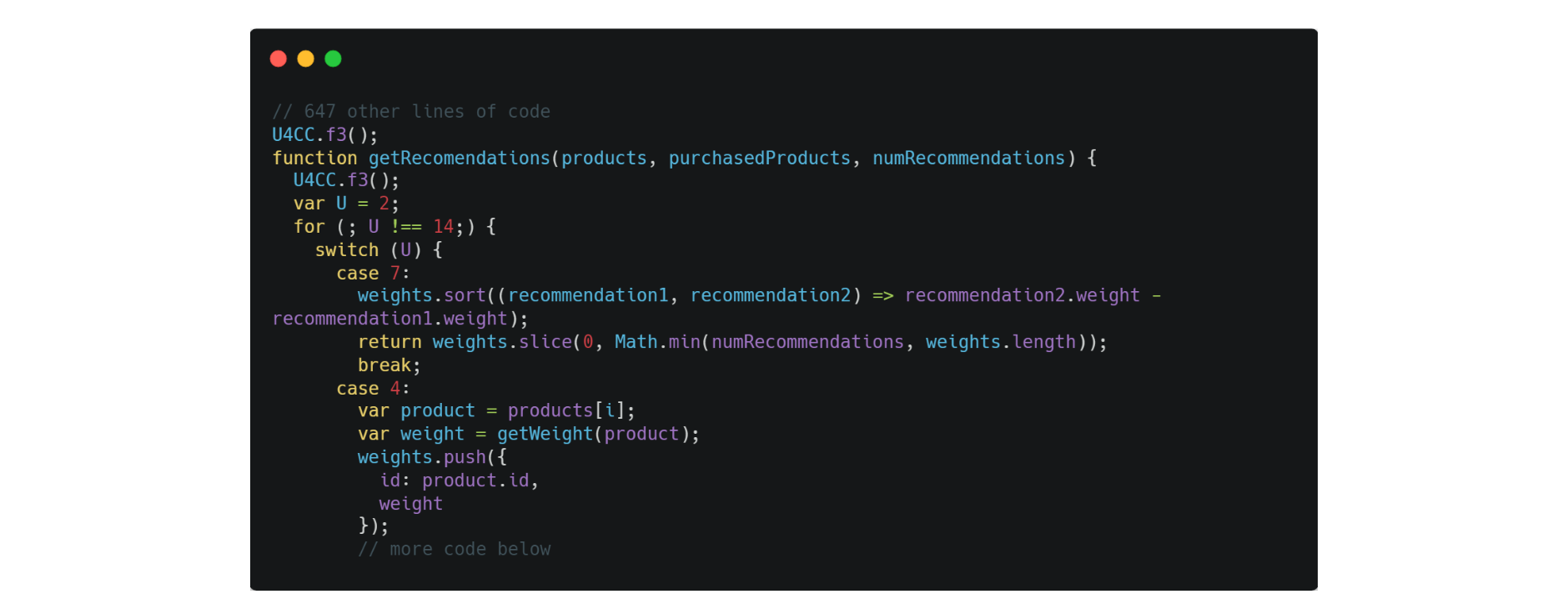
As such, with Jscrambler, we combine several different transformations, including string concealing and variable masking, to conceal the logic of the source code and prevent competitors from being able to retrieve any useful information.
After adding 11 different obfuscation transformations from Jscrambler, we get unreadable code that is difficult to reverse-engineer by humans and reverse-engineering tools.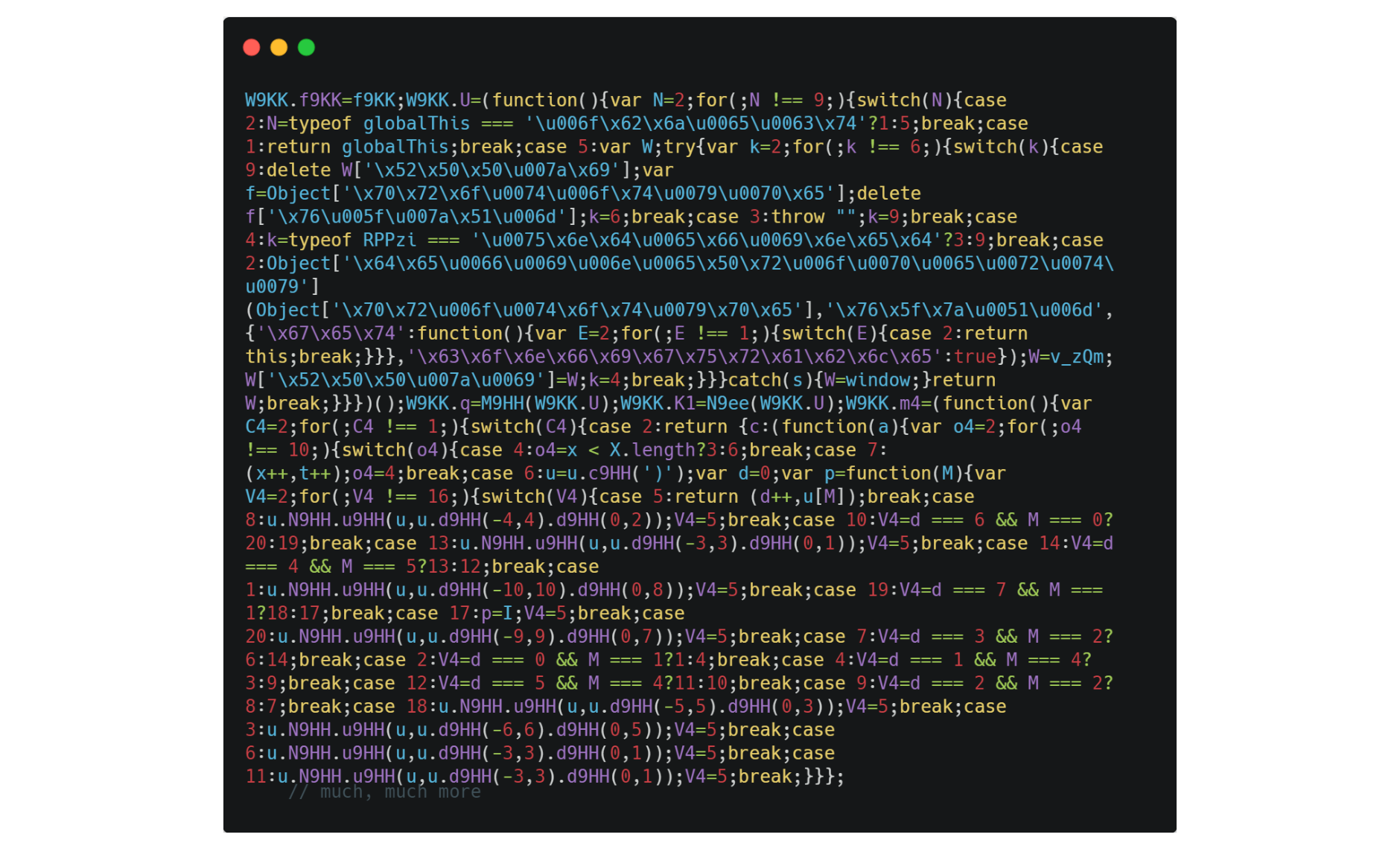
If you are motivated by protecting your intellectual property and keeping your algorithms safe from prying eyes, you would still want to raise the bar even higher to stop reverse engineering attempts.
By employing Jscrambler’s Self-Defending feature, your protected code will effectively mitigate any debugging or tampering attempt by triggering countermeasures at runtime, preventing dynamic code analysis. And since this is added on top of the potent obfuscation we saw before, it will also prevent static code analysis, leaving competitors completely locked out.
In case you’re only concerned about protecting specific algorithms throughout your source code, you can easily apply Jscrambler’s protection to these specific parts by using our Code Annotations feature.
Final Thoughts
As businesses become more digital and competition grows, the need to stand out is often translated into innovative digital products. Naturally, with innovation, and digital innovation specifically, we see Intellectual Property theft becoming more prevalent.
With that come the consequences that IP Theft brings to businesses, which shine a light on the fact that the cost of preventing it from ever unfolding is nowhere near the cost of trying to pick up the pieces afterward.
So, to protect their innovative proprietary algorithms, companies must protect their source code with strong obfuscation transformations, code locks, and runtime protection.
Jscrambler provides cutting-edge protection that, unlike simple obfuscation tools, is resilient to reverse-engineering both by humans and reverse engineering tools, ensuring that the code is kept away from prying eyes and can’t be redistributed.
Secure your JavaScript source code against theft and reverse engineering with a free Jscrambler trial.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
How to Protect Angular Code Against Theft and Reverse-Engineering
In this step-by-step guide, you'll learn how to protect your Angular code from being stolen or reverse-engineered, by leveraging the power of Jscrambler.
April 30, 2024 | By Antonello Semeraro | 13 min read
Protect Your Site Against Web Scraping
Known by a variety of terms like Screen Scraping, Web Harvesting, and Web Data Extracting, Web Scraping is a serious threat to companies in several sectors.
March 21, 2017 | By Shaumik Daityari | 6 min read
