Preventing Digital Skimming Attacks and Enabling PCI DSS Compliance
June 21st, 2022 | By John Elliott | 5 min read

Preventing skimming attacks is one of the reasons behind the newest version of PCI DSS.
E-commerce skimming, also known as form-jacking or Magecart attacks, represents the majority of criminal attacks against payment card data. They are simple to do and are hidden from the merchant or retailer and the cardholder.
In this blog post, let’s look at these attacks and the steps toward prevention.
Understanding the skimming attack
Any JavaScript running on a web page can access all data entered into form fields on that page.
Therefore, criminals want to have their own JavaScript loaded into any web page that collects payment card data. That way, their criminal JavaScript can transparently read the cardholder data as it is entered by the cardholder and send the data to a server controlled by them.
The attack can remain undetected for many months because it is completely silent and doesn’t interfere with the payment process.
The criminal can either place their malicious script in any JavaScript loaded from the company’s web servers, or they can insert their malicious script into the supply chain of any JavaScript that is loaded into the consumer browser from a third party or even a fourth party. The attack surfaces an e-commerce company has to manage is any JavaScript that is loaded into their web pages, whether that is from their web servers or any third parties.
Given the way that modern web applications are built, a web page typically contains 104 JavaScript libraries loaded from multiple locations. Every JavaScript is a potential entry point for the attacker, which means that the average web application provides dozens of different entry points that can be exploited by criminals.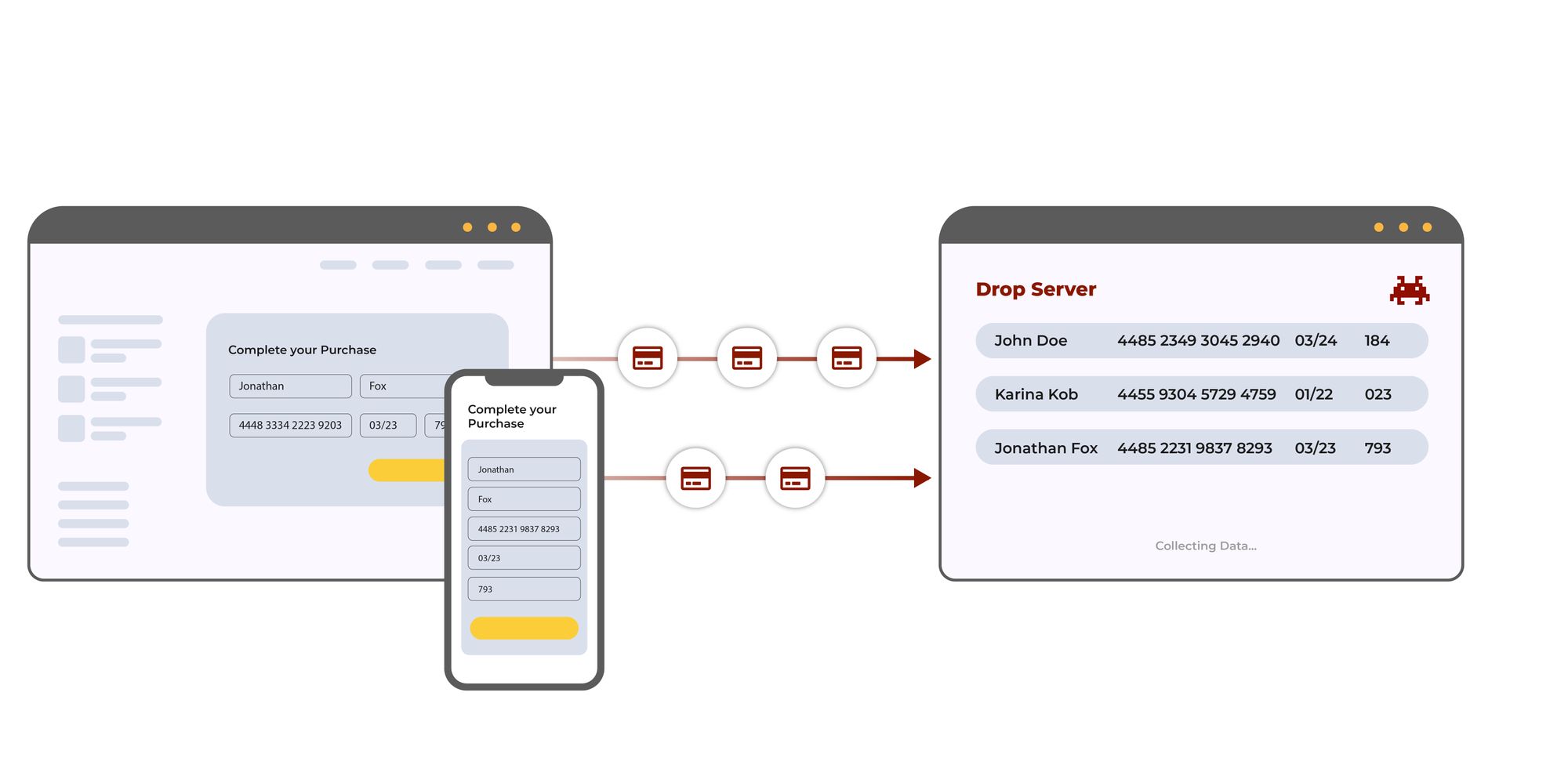
The new requirements in PCI DSS
The Payment Card Industry (PCI) Data Security Standard (DSS) is the industry standard applicable to all organizations that store, process, or transmit cardholder data or that can affect the security of cardholder data.
The standard is managed by the Payment Card Industry Security Standards Council (PCI SSC), which is enforced by card brands such as Visa and Mastercard.
The latest version of PCI DSS (v4) contains two new requirements to protect against and detect these E-commerce skimming attacks.
Requirement 6.4.3 (Preventative)
The first of these requirements (6.4.3) aims to prevent these attacks by limiting and managing the attack surface by ensuring that organizations:
Maintain an inventory of every script on the payment page;
Ensure that each script is approved and that the reason for the script’s use is documented;
Ensure the integrity of every script, so that the script loaded into the consumer’s browser hasn’t been tampered with or altered.
Requirement 11.6.1 (Detective)
The second requirement (11.6.1) requires organizations to detect unauthorized modifications (i.e., tampering) of any scripts and then produce an alert so the malicious script can be reviewed by the website owner.
Jscrambler’s client-side security platform enables compliance with both of the new PCI DSS requirements by providing a real-time inventory of scripts, validating the integrity of the script, and providing an alert when a script has been tampered with.
Additionally, Jscrambler goes one important step further than the requirement and will terminate the execution of any tampered script, therefore preventing a successful attack. In simple terms, Jscrambler provides JavaScript inventory management, tamper detection, and tamper prevention.
There are, of course, other ways of meeting these requirements, such as the use of a Content Security Policy (CSP) to define what scripts can be loaded and Subresource Integrity (SRI), which can validate the integrity of every script. However, these solutions are hard to implement and are both difficult and resource-intensive to maintain.
Jscrambler’s Webpage Integrity can be added to even the most complex websites in under a day and requires minimal resources to manage. An organization can outsource the management and response to any alerts to Jscrambler, which is an expert in detecting and defeating malicious JavaScript.
This new version of PCI DSS becomes mandatory on April 1, 2024. However, like many of the new requirements in the standard, the ones designed to defeat E-commerce skimming attacks will only become mandatory after April 1, 2025. Until that date, they are described as best practices.
The regulator’s view
Two high-profile E-commerce skimming attacks have resulted in regulatory action under the GDPR because payment card data is personal data.
In the case of British Airways, the skimming code was added to a library located on an internal web server. In Ticketmaster's case, the third-party provider of a real-time chat application was targeted by criminals.
In both cases, the failure of the company to put in place appropriate technical measures to prevent such skimming attacks was found to be a breach of the GDPR’s security principle by the UK’s Information Commissioner’s Office, which has commented on “the clear risk of third-party scripts within a payment page”.
Although the new requirements in PCI DSS are not mandatory until April 2025, they are indicated as “best practices” until this date. However, regulators are aware of the danger of skimming attacks, and organizations should consider whether, given the state of the art in protecting against such attacks by using products such as Jscrambler’s client-side security platform, implementing such protections in advance of the PCI DSS deadline would be beneficial to meet the test of “appropriateness” in GDPR.
Start with an inventory of JavaScript
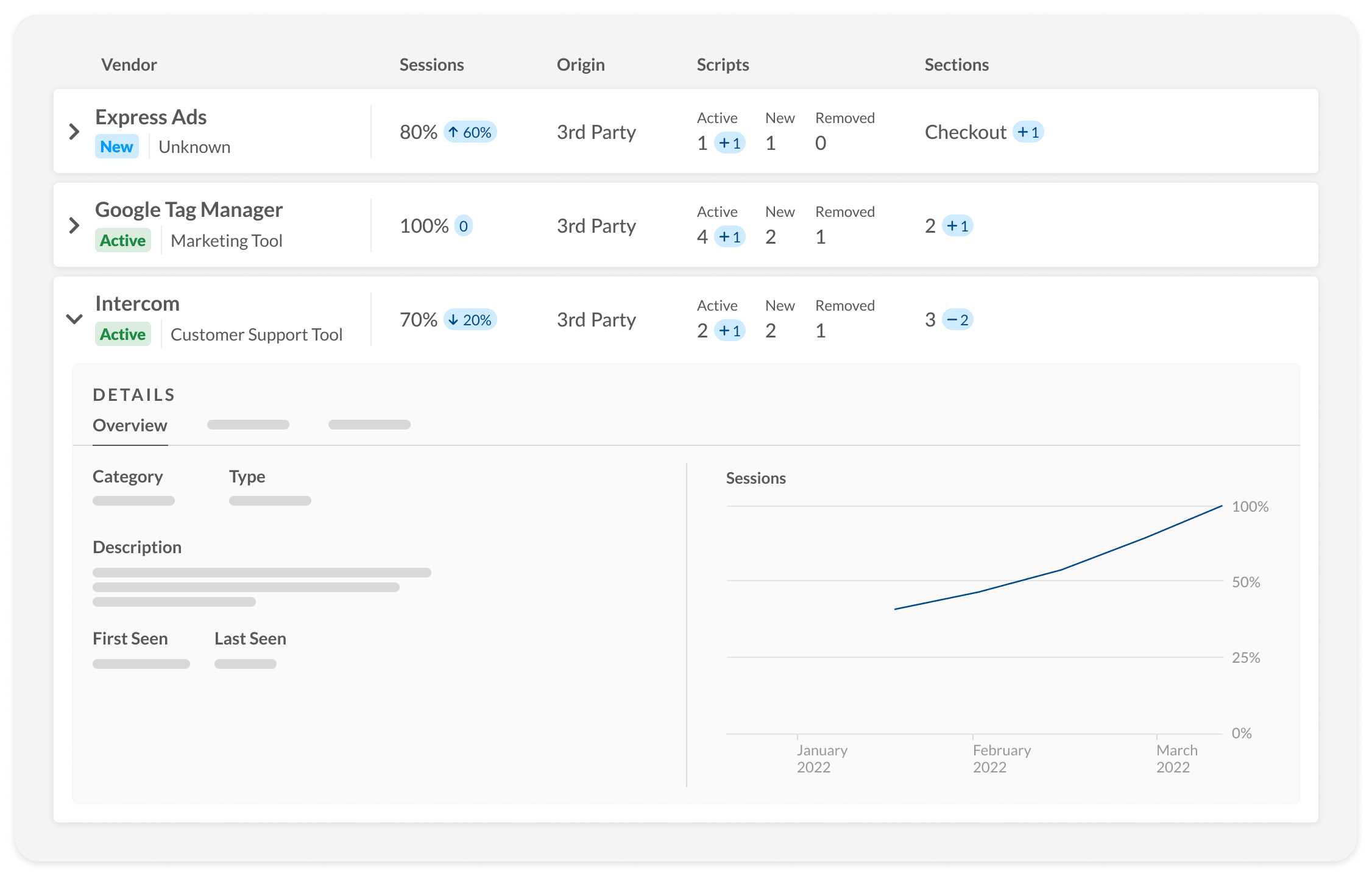
While the path towards compliance might at first seem strenuous, there’s a clear first step to satisfy the new requirements introduced in PCI DSS v4.0: creating an inventory of all JavaScript present in the website.
E-commerce applications contain many JavaScript modules and libraries, any one of which may be attacked by a criminal to include malicious JavaScript. So the first step for any defender is to understand the total JavaScript attack surface and answer these three questions:
What’s that script for?
Where is it being loaded from?
How much do I trust it?
Jscrambler’s Webpage Integrity creates an inventory of the JavaScript on your E-commerce site in real-time based on what’s seen in the consumer browser.
By having an inventory that is kept continuously updated, your organization gets full visibility of its exposure to third-party JavaScript and enables compliance with the new PCI DSS v4.0 requirements.
Take the first step towards client-side security and compliance today by requesting a free website inventory report.
Jscrambler's free PCI DSS Payment Page Analysis
This free PCI DSS Payment Page Analysis will assess your readiness for PCI DSS v4 payment page requirements 6.4.3 and 11.6.1. The only solution developed by
A PCI SSC Principal Participating Organization.
A member of the PCI SSC Board of Advisors.
A company with more than a decade of experience protecting JavaScript.
Try the PCI DSS Payment Page Analysis!
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
PCI SSC welcomes Jscrambler's CTO Pedro Fortuna to its Board of Advisors
Pedro Fortuna is one of 52 members of the 2023-2025 PCI SSC Board of Advisors.
June 12, 2023 | By Jscrambler | 4 min read
PCI DSS v4 Compliance: The Complete Checklist for Payment Pages
Ensure your e-commerce business meets PCI DSS v4. This complete checklist covers Requirements 6.4.3 and 11.6.1 for securing payment pages against e-skimming and Magecart attacks.
December 23, 2025 | By Nathan Coppinger | 15 min read

