Client-Side Path Traversal in SPAs
February 3rd, 2026 | By Abigail Amadi | 10 min read

Single-page applications (SPAs) are now an essential part of modern web development, delivering dynamic, responsive user experiences by loading a single HTML page and updating content via JavaScript. Nonetheless, they present security issues not found in other architectures because they use client-side logic, including client-side path traversal. This weakness allows attackers to use URL paths to fuzz for unauthorized routes or resources in an SPA, potentially disclosing sensitive data or bypassing security controls.
Understanding Client-Side Path Traversal
Client-side path traversal, also known as "on-site request forgery”, is a security vulnerability whereby an attacker exploits a weakness in the routing system of a single-page application (SPA) to access areas of the application that they are not authorized to access. It is as opposed to server-side path traversal, which uses manipulation of file paths (such as ../../etc/password) to access restricted files on the server. Conversely, client-side traversal focuses on the routing logic handled by frameworks such as React, Angular, and Vue.js.
Client-side routing handles navigation without full-page reloads, enabling SPAs. JavaScript determines which views to display based on the path. Unless this routing is appropriately secured, an attacker can manipulate URLs to access restricted pages, such as an admin dashboard or user data, without being intercepted. For example, a URL that includes /dashboard can be redirected to /admin if there are no access controls.
Typical scenarios include:
Direct URL manipulation: Users manually alter the browser’s URL to access restricted routes.
Query parameter abuse: Adding malicious values in an attempt to abuse the query parameters of the URL to deceive the routing system.
Insecure dynamic routing: Routes generated dynamically from untrusted input expose unintended endpoints.
Technical Mechanisms in SPAs
SPAs rely on client-side routing libraries (e.g., React Router, Angular Router, Vue Router) to map URLs to specific components or views. These libraries use browser APIs like the History API to manage navigation, updating the displayed content without server requests. While efficient, this architecture can be exploited if the routing logic is not carefully designed.
If the application does not enforce access controls, an attacker could navigate to /admin by modifying the URL, potentially accessing the AdminPanel component. The reliance on client-side logic means the server may not be consulted to validate access, creating a vulnerability.
Impact of Client-Side Path Traversal
Client-side path traversal may seem like a minor issue at first, but its effects can be both short-term and long-term. Below are the key risks it introduces:
Unauthorized Access to Sensitive Details: Attackers may bypass the application's standard navigation and authentication experience, enabling them to access hidden application routes, such as administrative pages, the user dashboard, or system settings.
Exposure of Confidential Data: Insecure routes may expose personal user information, access tokens, or stored content that should be accessible only to authenticated users.
Circumvention of Client-Side Access Controls: When access control is implemented solely in frontend logic, attackers can use URLs to bypass these controls and potentially escalate their access.
Launching Point for Compound Attacks: Path traversal can serve as a gateway to other vulnerabilities, including Cross-Site Scripting (XSS) or unauthorized API calls, leading to a more severe compromise.
Compliance Violations and Reputational Damage: Sensitive data disclosure can violate privacy laws such as GDPR, CCPA, and HIPAA, leading to lawsuits and reputational harm.
Causes of Client-Side Path Traversal
Vulnerabilities in client-side path traversal often stem from a combination of routing logic and overreliance on client-side controls in Single Page Applications (SPAs). Common causes include:
Unvalidated URL Parameters: For route parameters (e.g., /user/id), accepting such parameters without necessary validation or sanitization allows an attacker to inject restricted values and access raw components or data. Insecure Dynamic Routing: Route building based on the user input, say navigate("/" + userInput) will reveal routes accidentally showing internal pages that should not be accessed by the user.
Lack of Input Validation in Routing Logic: Routing logic lacks rigid input validation; an attacker can exploit this vulnerability to craft URLs that trigger routing behavior to access restricted content.
Overly Permissive or Misconfigured Routes: Wildcard or catch-all routes may be used without adequate protection and can create backdoor access to sensitive application areas.
Sole Reliance on Client-Side Authorization: Authorization that performs role checks or access control at the browser level, typically storing local storage or JavaScript variables, are easily compromised by attackers.
Example of Vulnerable Routing
Unsafe Construction: JavaScript code builds request URLs dynamically, e.g.:
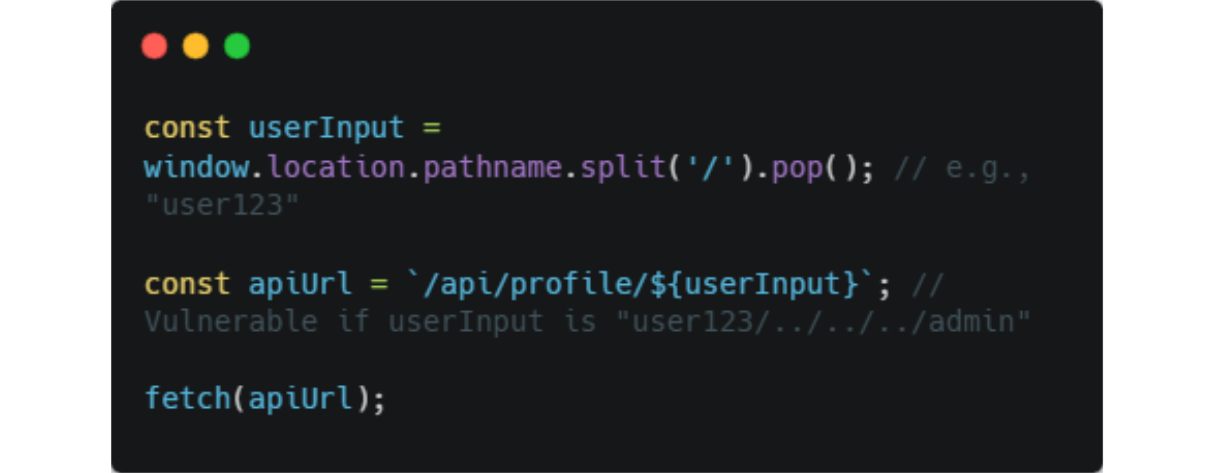
Here, injecting user123/../../../admin resolves to /api/admin, bypassing intended routes.
Defending SPAs Against Path Traversal
Preventing client-side path traversal in SPAs requires a defense-in-depth approach. Developers should enforce strong validation, route control, and server-side checks to ensure application integrity.
1. Validate and Sanitize All Inputs
Never trust URL parameters or client-provided data. Use strict input validation for dynamic route values. Rely on whitelists or patterns (e.g., regex) to ensure parameters like /user/:id follow safe formats (e.g., UUIDs or integers). Example:
const isValidId = /^[0-9a-f]{24}$/i.test(userId); if (!isValidId) return <Navigate to="/not-found" />; 2. Use Secure, Static Route Definitions
Avoid building routes dynamically from untrusted input. Instead, define routes explicitly.
Vulnerable:
navigate("/" + userInput); // dangerous
Safe:
<Route path="/user/:id" element={<UserProfile />} /> Inside the UserProfile component, validate the id before fetching or rendering data.
3. Enforce Server-Side Authorization
Client-side checks alone are not enough. Always validate user roles and permissions on the backend before returning protected data. Use authenticated API calls that enforce RBAC/ABAC server-side, even if the frontend hides or protects certain routes.
4. Implement Role-Based Access Control (RBAC)
Design your app to respect permission boundaries across both client and server layers. Use a centralized auth hook or service that fetches user roles from the backend and keeps them immutable from the frontend.
5. Perform Regular Security Testing
Include security reviews in your CI/CD pipeline, such as running static analysis tools (like ESLint security plugins), conducting pen tests, using dependency scanners, and manual code reviews focused on routing and auth logic.
How Jscrambler Curbs Client-Side Path Traversal
Jscrambler is a comprehensive client-side protection platform that goes beyond code obfuscation to help prevent client-side path traversal and related attacks. Its increased functionality makes it harder for attackers to exploit the SPA's routing logic, providing a strong defense-in-depth approach. The following are some of the important Jscrambler properties that can be used to curb this vulnerability:
Advanced Code Obfuscation
Polymorphic obfuscation with Jscrambler takes readable JavaScript code and converts it into an unreadable format that is hard for attackers to reverse-engineer and that prevents the engine from modifying routing logic or sensitive variables. As an example, such variables as userRole or routing paths in the previous vulnerable code are masked, which makes finding and using client-side logic less likely for attackers.
.png)
After Jscrambler’s obfuscation, the code might resemble (simplified representation): .png)
This obfuscation complicates attempts to manipulate client-side checks or routing paths.
Runtime Protection and Anti-Tampering
Jscrambler’s runtime protection includes anti-tampering and anti-debugging mechanisms that detect and respond to attempts to modify or analyze the application’s code at runtime. If an attacker tries to alter client-side routing logic (e.g., by modifying the DOM or injecting malicious scripts), Jscrambler can trigger countermeasures such as:
Breaking the application: Rendering the application unusable if tampering is detected.
Custom callbacks: Executing a predefined function to log or block unauthorized actions.
These features make it harder for attackers to bypass client-side checks or manipulate routes dynamically.
Real-Time Monitoring and Notifications
Jscrambler offers real-time monitoring and warnings for suspicious activity, including unauthorized access to routes or attempts to compromise client-side logic. This enables developers to monitor and address path traversal attempts in a timely manner, thereby limiting the time attackers have to exploit.
Jscrambler integrates with any modern SPA development workflow, including frameworks such as React, Angular, and Vue.js. Developers can integrate Jscrambler into the build process, using tools such as Webpack or CI/CD pipelines, to protect routing logic and sensitive code before deployment.
Conclusion
Path traversal is a critical weakness in SPAs, as it can lead to unauthorized access and data exposure. Developers can significantly mitigate risk by understanding its causes, implementing robust mitigation strategies, and using powerful obfuscation, runtime protection, and code-locking tools, such as those offered by Jscrambler. To obtain SPAs, both client- and server-side protection, frequent testing, and developer awareness are required. Since SPAs are still dominant in web development, it is imperative to prioritize security and provide holistic protection by using these tools and methods to keep users secure and maintain credibility.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
AI-Powered JavaScript Attacks: The New Threat Landscape for 2025
In 2025, JavaScript and artificial intelligence converged, marking the beginning of a new era of advanced cybercriminalization. Cybercriminals no longer use a manual approach. Payloads are now...
November 11, 2025 | By Ejiro Thankgod | 13 min read
Jscrambler WPI 101 - Getting Started
Jscrambler’s Webpage Integrity (WPI) defends against targeted risks by safeguarding web assets and payment pages against supply chain attacks, data exfiltration, DOM tampering, and more, while...
January 21, 2026 | By Jscrambler | 7 min read
