[Case Study] Jscrambler Helps Neobanks Protect JavaScript
June 9th, 2021 | By Jscrambler | 5 min read
![[Case Study] Jscrambler Helps Neobanks Protect JavaScript width=](/img/containers/images/blog-images/jscrambler-helps-neobanks-protect-javascript-case-study.png/d88a375a0f1e0a890bbb2eeb947068b7.webp)
Jscrambler helps Neobanks protect JavaScript to overcome security challenges in the banking and financial services industries.
Leading Neobanks like Revolut, Nubank, and Starling Bank keep challenging the banking industry and setting new standards. However, these Neobanks have challenges to address, specifically application security.
Today, we explore a case study on how Jscrambler has helped Neobanks protect their JavaScript and overcome some common challenges in their industry.
Note: We have anonymized all company and personal names.
Neobanking Model: From Innovation to Satisfaction
Neobanks defy traditional banking by betting everything on digital and delivering customer-centric services for payments and money management.
73% of consumer interactions with banks are done digitally.
While traditional banks have invested in Web and mobile platforms, Neobanks release twice as many new features and three times more app updates per year.
They also run 42% faster than incumbents. As a result, user satisfaction ratings for Neobanks in the US (90%) are much higher than those of traditional banks (66%).
Neobanks’ technological flexibility comes from investing in cloud-based infrastructure and advanced Web and mobile applications using modern JavaScript frameworks such as React Native.
This allows for cutting product development costs and time, paving the way for rapid iteration and innovation, aided by relying on third-party integrations instead of developing all pieces of code in-house. However, this approach raises additional concerns about application security.
Faster Development, Larger Attack Surface
In software development, pursuing agility and speed often means widening security gaps.
Neobanks must be aware that client-side JavaScript can be targeted by attackers, despite JavaScript’s advantages. This may lead to intellectual property theft, code tampering, application abuse, and data exfiltration.
Unless protected with an enterprise-grade solution, this exposed JavaScript poses a business threat.
Jscrambler and Neobanks: Managing Application Security
The Challenges
Over the last few years, Neobanks, mainly from North and South America, have come to Jscrambler with significant security challenges.
With web and mobile apps built using JavaScript and an incidence of the React Native and Ionic frameworks for cross-platform mobile development, security teams understood early on that client-side logic would be a security liability.
"Protecting our JavaScript was a requirement from day one. Investors and management made sure that it was a priority. Today, not a single product ships without secure client-side logic.".
There was a high likelihood of having to run sensitive logic on the client-side. Therefore, it became paramount to guarantee that this logic would be concealed with the most potent and resilient technology available today.
Therefore, it was mandatory to ensure that automated reverse-engineering tools would always fail to reverse the concealed code, as it would be unfeasible for attackers to achieve it manually. This goes hand in hand with the security recommendations from the OWASP Mobile Application Security Verification Standard (MASVS).
As these Neobanks’ apps handle valuable services, another key challenge was guaranteeing that malicious actors wouldn’t be able to tamper with the code. JavaScript had to react at runtime to mitigate these attacks.
And since both the Web and mobile apps handle sensitive data, credentials, personally identifiable information, and financial details, an additional pre-eminent requirement was guaranteeing that JavaScript couldn’t serve as a gateway for attackers to plan attacks that would steal user data.
"We’re called “challenger banks” for a reason; one of our toughest challenges is still gaining customer trust. When handling their data, we can’t just meet the minimum requirements; we must excel at it and keep data safe at all costs."
With each Neobank possessing more than one application, it was also essential to guarantee that JavaScript protection would fit seamlessly into their CI/CD and integration tests.
The Solution
Given the challenges these Neobanks were facing, they had to meet the highest standards for JavaScript protection with an on-premise solution.
Polymorphic obfuscation
The first step towards securing JavaScript was Jscrambler’s polymorphic obfuscation.
With this security layer, all of the source code of the Neobanks’ apps was concealed beyond possible recognition.
Jscrambler’s set of the most potent and resilient transformations guaranteed cutting-edge obfuscation.
Its inherent polymorphism ensured that each new code deployment would be completely different, making it an extra line of defense against reverse engineering attempts.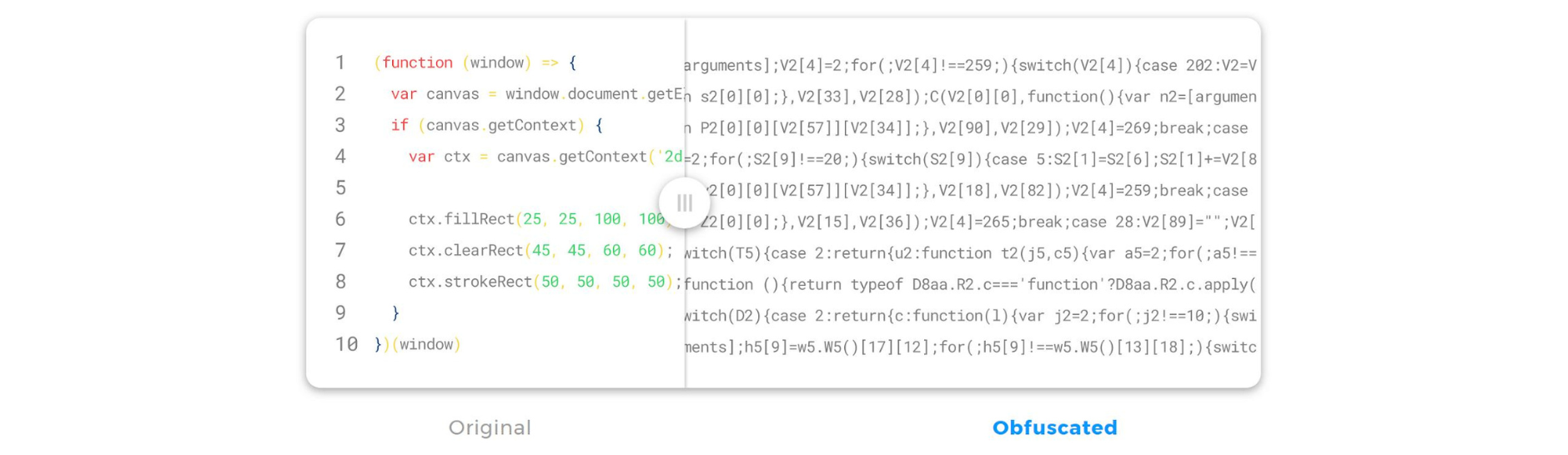
"The concealed code looks like absolute nonsense and passed all of our tests. Being able to pick from dozens of well-documented transformations and fine-tune each one was very important."
Following obfuscation, these Neobanks leveraged an additional Jscrambler security layer to meet the challenges of preventing application tampering and client-side data exfiltration: self-defending.
With this runtime protection, their apps gained a series of integrity checks that detect every debugging attempt and break the app whenever tampering occurs.
Taking advantage of other client-side countermeasures, such as calling a custom function, has enabled these Neobanks to stop malicious users.
Neobanks’ Security Engineers were well aware of the problem and the required steps for solving it.
After the initial setup of their Jscrambler instance, it took on average 1 week and 2 meetings with Jscrambler’s Engineers to integrate Jscrambler seamlessly into their CI/CD pipeline. From there, Jscrambler became an automated part of their application build process.
"The Jscrambler team has extensive knowledge of JavaScript. Communication with our engineering teams was excellent, and all issues were solved very quickly."
The Results
5 Web and Mobile applications were secured in one week
Securing JavaScript code, first and foremost, requires awareness of the threats caused by having logic exposed on the client-side. Neobanks felt this pain from the very onset of the business, as their assets depended upon it.
By opting for Jscrambler’s JavaScript protection technology, product teams met their main requirement of integrating a code protection solution into their CI/CD. Now, these Neobanks deploy secure code to production, knowing each build has a fresh set of the most potent and resilient JavaScript protection available today.
"Today, not a single product ships without secure client-side logic, and this has been extremely effective."
In parallel, security teams were able to fulfill several security recommendations by OWASP, namely the OWASP Mobile Top 10, which states that “To prevent effective reverse engineering, you must use an obfuscation tool” and “The app must be able to react appropriately at runtime to a code integrity violation.”.
To management, ensuring that their applications’ source code was protected against reverse engineering and tampering meant a new competitive advantage.
With Jscrambler, Neobanks gained the upper hand in future funding rounds.
In an industry where numbers are everything, for these Neobanks, Jscrambler’s outcome couldn’t be rounder: 0 integration issues and 0 successful attacks on JavaScript code.
Conclusion
To maintain their edge in the banking race, Neobanks need to maintain the integrity and security of their applications.
To do it, they need enterprise-grade solutions that offer them the flexibility and ease of implementation they need to continue innovating.
If you also want to secure your JavaScript source code against theft, reverse engineering, and more, you can try our solution for neobanks for free.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Online Banking and Financial Services: Is Enough Being Done to Protect the End-User?
Working in online banking and financial services? Check what you should address to protect your users according to Information Age.
August 16, 2017 | By Jscrambler | 5 min read
Regulations in Digital Banking: White Paper for Banks Compliance
Our white paper about banks compliance in the digital landscape explores how firms can increase compliance with regulations like PSD2, 23 NYCRR 500, GLBA, and GDPR for improved data privacy.
May 19, 2020 | By Jscrambler | 2 min read
