Insights From a Crypto Wallet Phishing Attack
April 16th, 2021 | By Pedro Fortuna | 9 min read

Today, we give you insights from a Crypto Wallet Phishing Attack.
How did scammers use the source code to perpetrate a phishing attack against the cryptocurrency wallet Celsius?
Celsius Email System Breach
In the early hours of April 14, users of the rewards-earning cryptocurrency platform Celsius Networks started reporting a suspicious email that they received.
The email appeared to be a legitimate one coming from Celsius. It announced the launch of the anticipated “Celsius Web Wallet”, along with an offer of $500 in CEL to users who followed a promo link.
The email (you can see it below) presented no indication of being fake and was indistinguishable from a plausible launch campaign by the company.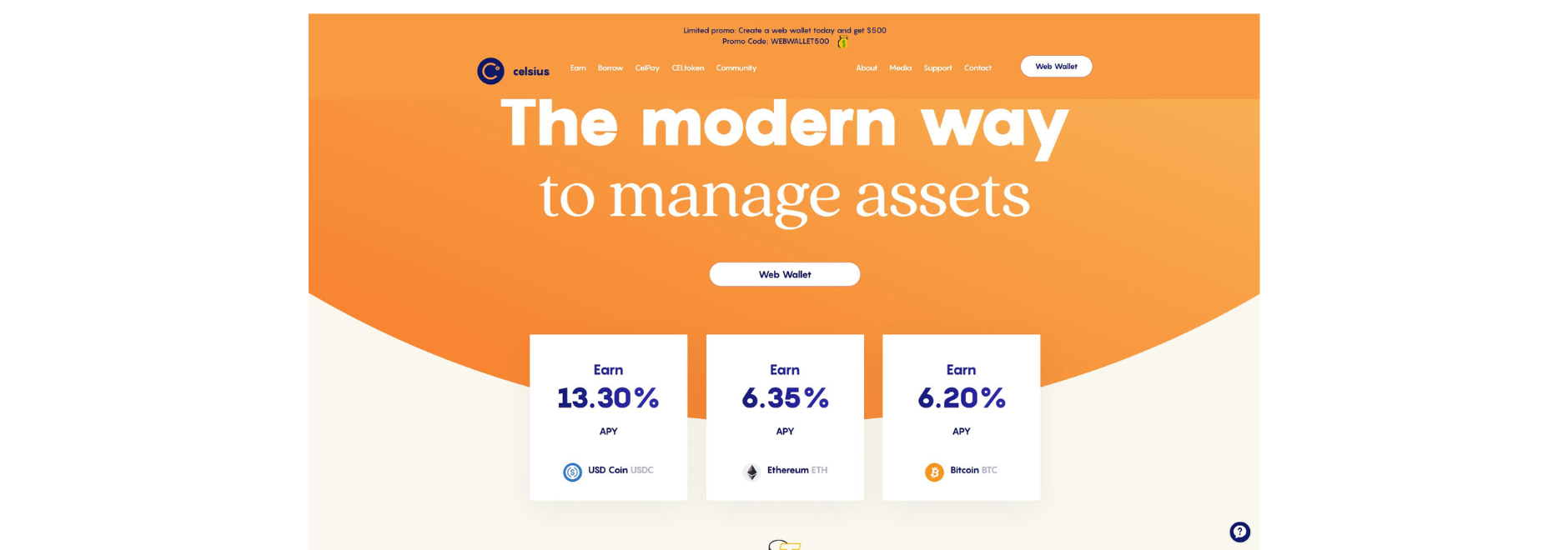 However, as some attentive users soon realized, the link led them to celsiuswallet.network instead of the official company domain, celsius.network.
However, as some attentive users soon realized, the link led them to celsiuswallet.network instead of the official company domain, celsius.network.
This was a clear indication that something was not right, as Celsius has long made it clear that the company does not use any other official domain.
Unfortunately, since the destination page looked like a legitimate company page, several users went ahead in their attempt to claim the offer, submitting sensitive information.
Soon after, reports started appearing of users who claimed to have lost their crypto balance, and many more said they received the phishing email and even SMS messages all linking to the same fraudulent page.Celsius diligently kept on top of the incident, warning users about the scam email and advising them on what they should do to remain secure.
The company disclosed that its security team identified a data leak on a third-party service containing some of its users’ data, which is likely how the scammers gained access to valid emails and phone numbers.
This attack posed several important questions:
What does the code of the fraudulent page look like, and what does it do?
What type of preventive measures can companies put in place to avoid these scam copycat pages?
What does this incident say about third-party management?
Because our research team is actively engaged in uncovering details about these types of attacks, they were able to analyze the complete source code of the scam page.
We will go over some key insights as to who may be behind the attack, how the attack worked, and how similar companies are at risk of losing user data to web supply chain attacks.
Dissecting a Pristine Copycat
We have been seeing a trend where phishing attacks are getting more sophisticated. Scammers are doing a thorough job of writing seemingly official company emails and enticing users to submit valuable information on a scam page.
This incident with Celsius is especially interesting because the scammers leveraged users’ latent expectations of a web wallet launch.
Not only that, but they managed to create a scam page that looks like a perfectly believable company page. It uses design elements that are identical to those of the official page and follows a similar structure, with no discernible suspicious elements on the page itself, at least at first glance (in other words, a pristine copycat).
To analyze how this copycat was built and what it does, our research team went through its source code. We found a complete visual replica of the Celsius website assets and a testjs.js file which the attackers used to load fancybox (a library that enables additional page customization) features.
Although the scammers copied the assets perfectly, they kept themselves from using the same CMS used by Celsius and instead copied the main page from the official website, adapting it to their needs.
Inside this testjs.js file, we found some interesting comments written in Portuguese, which hints that the attackers may be from a Portuguese-speaking country (Portugal, Brazil, Angola, etc.).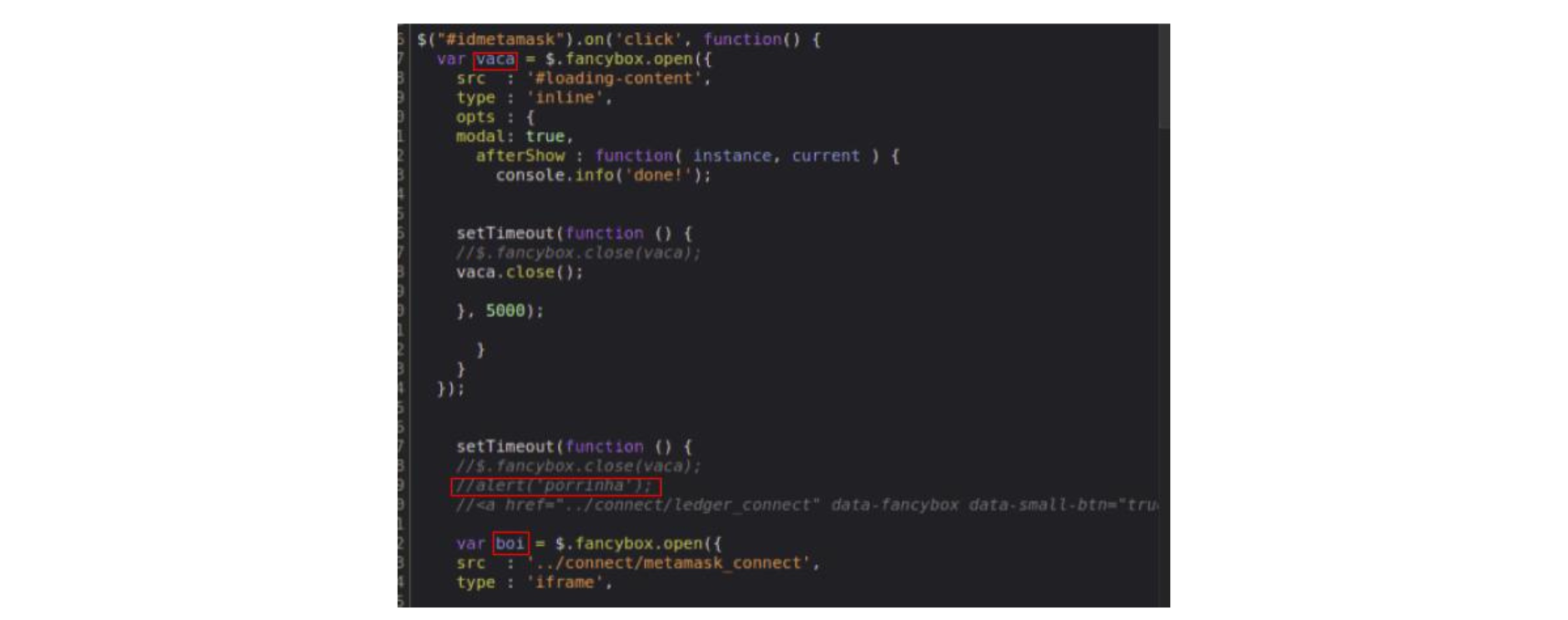 Looking at the HTML files, we also found evidence that the code was copied without much care. Namely, we found comments that are specific to Celsius CMS. Since the attackers did not use the same CMS, it would not make sense to have this in the HTML body, so they probably forgot or didn't care to remove it.
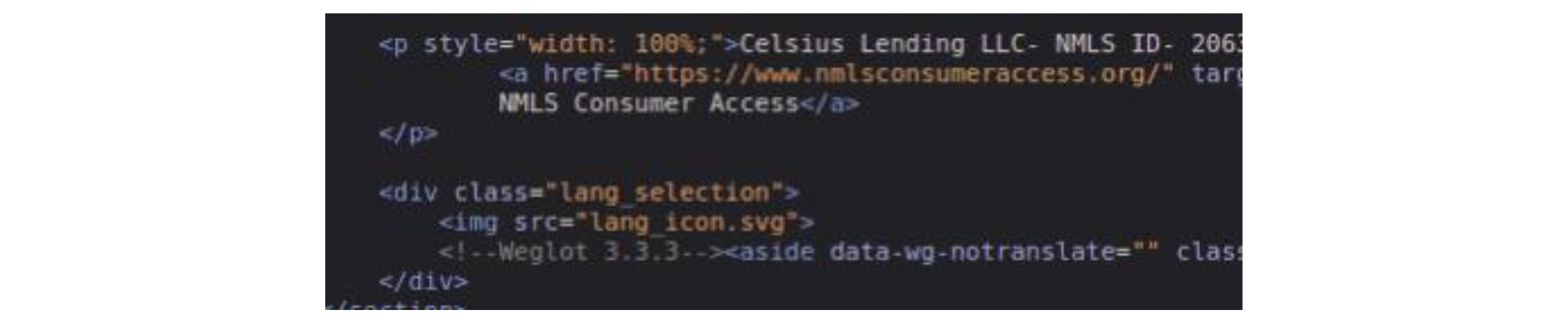
Looking at the HTML files, we also found evidence that the code was copied without much care. Namely, we found comments that are specific to Celsius CMS. Since the attackers did not use the same CMS, it would not make sense to have this in the HTML body, so they probably forgot or didn't care to remove it.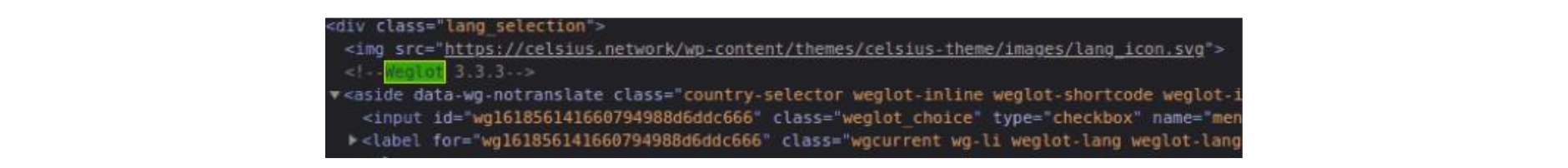
 Regarding what happens on the scam page when a user clicks the Web Wallet button to claim the (alleged) offer, we see a fancybox pop-up appear asking the user which wallet they want to connect to.
Regarding what happens on the scam page when a user clicks the Web Wallet button to claim the (alleged) offer, we see a fancybox pop-up appear asking the user which wallet they want to connect to.
The behavior afterward is always the same: the user inserts the details of their wallet and, after clicking on “Import Wallet”, the page says it had a problem connecting to the wallet of choice.
It is important to note that, during our research, this behavior occurred when we provided fake wallet information, so it’s possible it could be different when a user-provided a real wallet.
Upon pressing the Import Wallet button, the wallet details the customer introduced are parsed by the space.js script. We found that space.JS was the only file that had been obfuscated by attackers, which led us to believe that the file could contain some more useful information on the attack.
Deobfuscating the script
We deobfuscated the script, and the resulting code shows us that the attackers used at least 3 domains in their skimming campaign: celsiuswebwallet.network, celsiuswallet.network, and walletweb.xyz (the corresponding websites are already offline at the time of writing).
The.xyz domain was registered on November 25th, 2020, and the other domains on March 31st, 2021. These dates may hint that the attacker was already working on the MO website in November last year but only very recently adapted the website to the Celsius look and feel. The attacker will probably try to reuse the same codebase in other similar phishing attacks in the future.
We also noticed the usage of several anti-debugging and anti-tampering techniques (shown below) and the EmulateTab API to focus victims' cursor and attention on the form.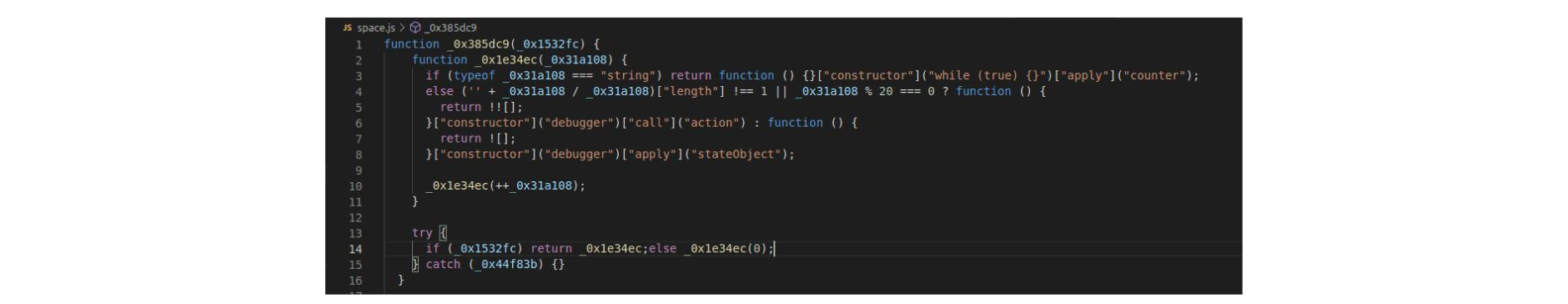
 The anti-debugging technique is found in the deobfuscated code.
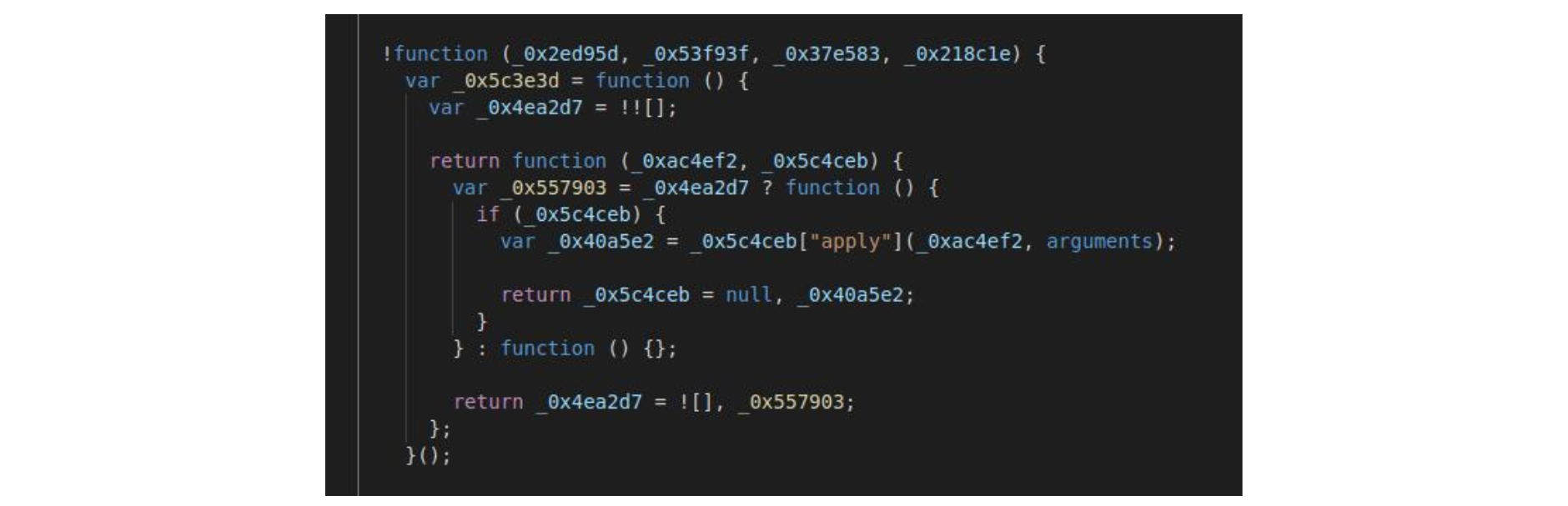
The anti-debugging technique is found in the deobfuscated code.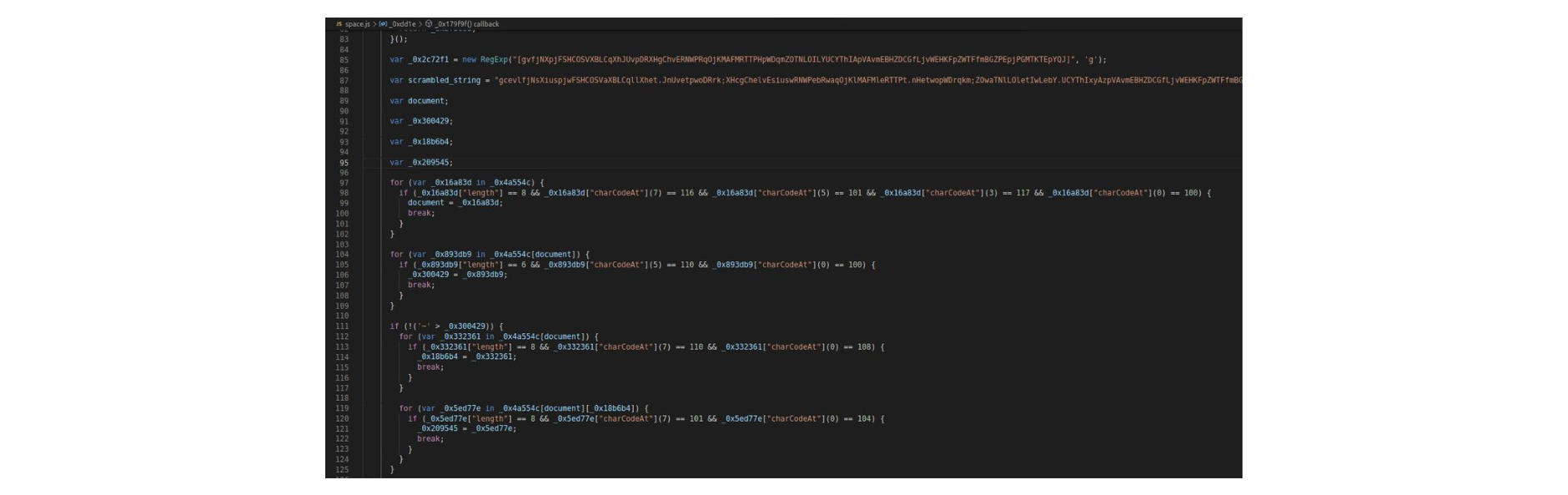 The anti-tampering technique found in the deobfuscated code is:
The anti-tampering technique found in the deobfuscated code is: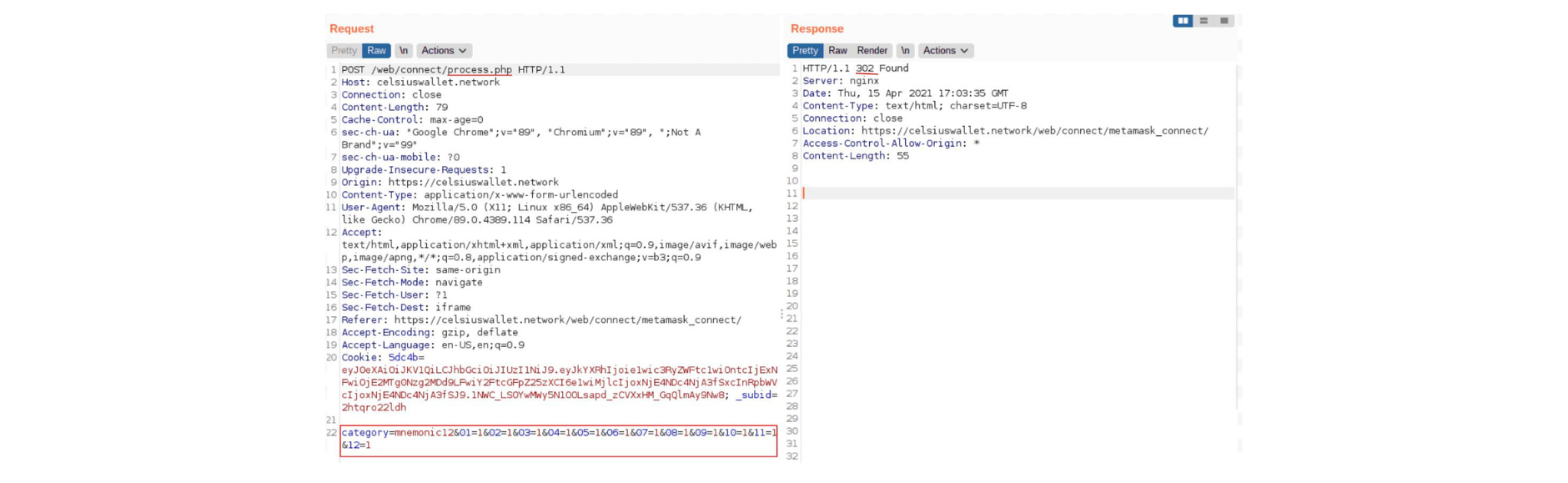 After being parsed by space.js, the data was sent to the process.php file (request shown below) to be processed by the attackers.
After being parsed by space.js, the data was sent to the process.php file (request shown below) to be processed by the attackers.
At this point, the attackers can do whatever they want with the collected data.
After analyzing the flow of the whole scam, several signs point out that this was performed by attackers with experience in this type of attack.
They meticulously chose a domain that was similar to Celsius’ and were able to create a credible email and copycat page.
Plus, since there’s some degree of sophistication required to use leaked customer emails as part of the campaign, and because we found a reference to an advertising domain called adsymptotic.com, this might indicate that the attack was a result of collaboration between groups and/or individual attackers, perhaps part of a larger ongoing phishing campaign.
Preventing Scam Copycat Pages
Considering all the files of the scam page that we analyzed, we conclude that the JavaScript source code of the scam page is distinct from the source code of the official Celsius page. It appears that they did indeed copy or mimic the HTML and CSS source code but did not copy any of the JavaScript logic of Celsius’ platform.
However, this is not always the case. If attackers, for some reason, choose to copy the entire source code, some preventive measures can raise the cost of creating the copycat page.
Protecting the website source code with runtime defenses will make it much more difficult for attackers to retrieve the source code. These runtime defenses not only prevent the use of debuggers but also derail execution if the protected code is changed (which would be the case when attackers want to create a new scam landing page).
Additionally, it’s possible to protect this same source code with domain locks that, when coupled with real-time notifications, trigger a critical security warning when someone attempts to run the code outside of the official company domain.
These are not foolproof measures, as it’s technically impossible to ensure that a website’s source code can’t be retrieved or reused by attackers. But the key takeaway is that these security controls can increase the cost of the attack to the point where scammers are more likely to move on to other targets.
Gaining Access to User Data
As disclosed by Celsius, “an unauthorized party managed to gain access to a third-party email distribution system to send a phishing communication through email and SMS to some Celsius customers and others”. This pinpoints the origin of the leaked data to a compromised third party—in other words, a supply chain attack.
Our discovery of a reference to the adsymptotic.com domain appears to indicate that this might be part of a bigger phishing campaign. As such, this attack may be replicated on similar crypto wallets (Nexo, BlockFi, Compound, and Crypto.com), especially if the payoff from the Celsius incident keeps growing.
To be successful, the attack would require gaining access to the legitimate emails and phone numbers of those platforms’ users. Similar to how attackers achieved this in the Celsius incident, by leaking data from a third-party email service, they could next turn to web supply chain attacks, a typical weak link in companies' websites.
By infiltrating one of these websites’ third-party script providers (such as a chatbot or an analytics service), attackers would be able to run malicious code on the website itself, covertly collecting fresh batches of user emails and phone numbers. Rinse and repeat.
Third-Party Management in the Web Supply Chain
The issue of (in)security in the web supply chain derives from the fact that, within the context of a web page, all scripts have the same privilege, regardless of whether they are first- or third-party.
As a result, any third-party script can:
Harvest any user input;
Add extra code;
Hijack events;
Fully modify the behavior of the web page, tricking users into doing actions against their interests;
Tamper with other code in the same scope.
Contact any external domain and exfiltrate data.
All of these events can happen without any awareness from the user or the website owner. As a result, when a third-party script gets compromised, the attack typically remains undetected for weeks or even months, giving attackers plenty of time to exfiltrate valuable user data.
Celsius already made it clear that the company will take action to ensure strict third-party management, stating that they “will raise the bar on what we require from third parties in terms of ISO and SOC certifications.”
Companies must go the extra mile here, meticulously vetting third-party scripts and implementing security measures that give them visibility and control over these third-party scripts.
Final Thoughts
The Celsius attack might seem like any other phishing scam. However, as our research found, this is a prime example of a pristine copycat page being leveraged to trick users and eventually steal their crypto balance.
The evidence points out that this could be part of an ongoing phishing campaign with additional targets.
Jscrambler researchers have been investigating these types of attacks and working closely with companies to help them gain visibility and control over their third parties.
With cryptocurrencies displaying such momentum, all crypto platforms must step up their security, employing a defense-in-depth approach with effective client-side security controls.
Seeing how phone numbers were also compromised, we advise Celsius users to be aware of scams like SIM swapping, which can compromise SMS-based 2FA.
As for users of similar crypto wallets, we advise reviewing their account security measures (enforce 2FA, use strong passwords, and update them regularly), being extra cautious when clicking links only from official domains, and closely following the official company channels.
With the cryptocurrency market fully bullish, the upside of successful attacks is far too appealing for attackers.
They already have the code developed and can rapidly pivot to new sites. We should expect more of these pristine phishing scams in the future.
Jscrambler
The leader in client-side Web security. With Jscrambler, JavaScript applications become self-defensive and capable of detecting and blocking client-side attacks like Magecart.
View All ArticlesMust read next
Phishing Attacks Against Android Instant Apps
Instant Apps take Android to new heights, blurring the separation between web and native. This sounds exciting, but what are the implications?
March 7, 2017 | By Camilo Reyes | 4 min read
Browser-in-the-Browser: A New Wave of Picture-in-Picture Phishing Attacks?
In this blog post, we are going to talk about the browser in the browser (BitB) attack and the different approaches used in this deception technique.
April 22, 2022 | By Jscrambler | 5 min read
